In this blog, we will show you the steps to create AWS VPC Peering across Region environment. VPC Peering allows traffic from VPC1 to be sent to VPC2, based upon the network address of the particular resource.
AWS VPC Peering Across Region
Environment Overview
For this, we are connecting two VPC’s between Tokyo and Ohio. In the Mumbai region, I have created a VPC with two subnets in a different availability zone.
How to Create VPC
1- Login with AWS account, go to the AWS Services tab and then select VPC under Networking & Content Delivery.
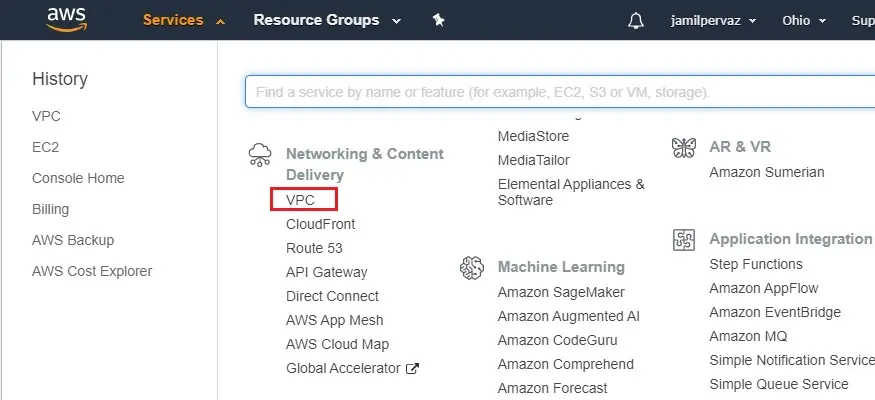
2- Under Virtual Private Cloud select Your VPCs
Click on Create VPC.
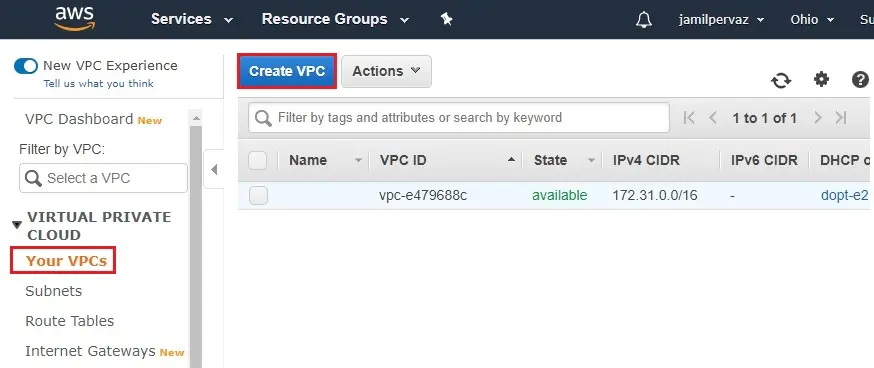
3- Create VPC wizard,
Name tag – VPC-Ohio.
IPv4 CIDR block – 192.168.0.0/16.
Tenancy – default
Click Create
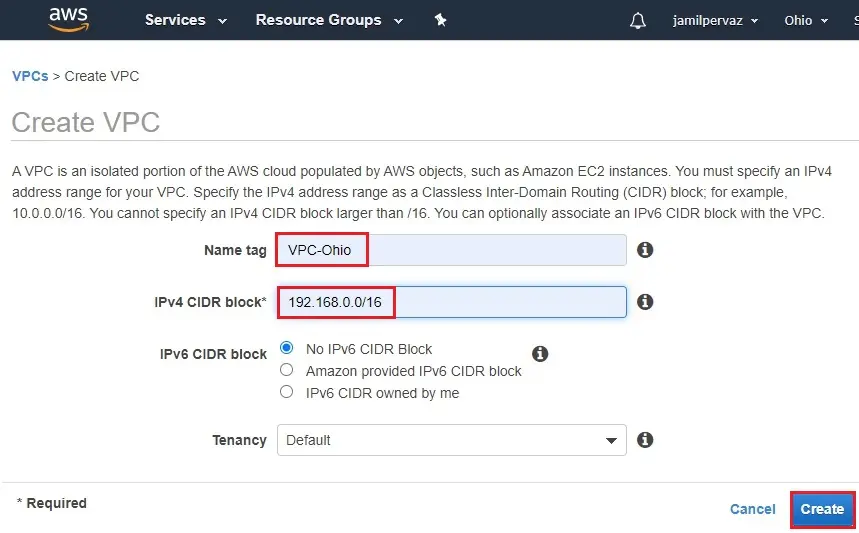
4- Click close
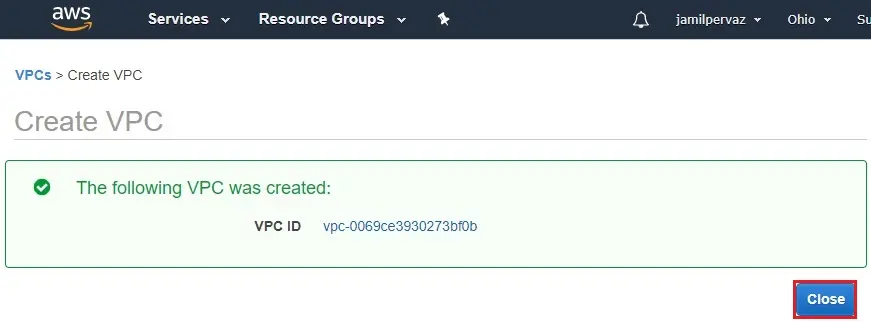
5- Now you can see VPC successfully created in the Ohio Region.
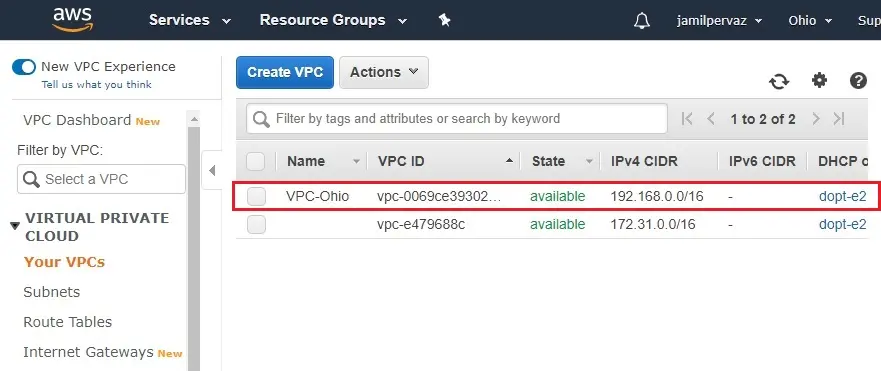
Create Subnet
1- Select Subnets.
Choose Create Subnet.
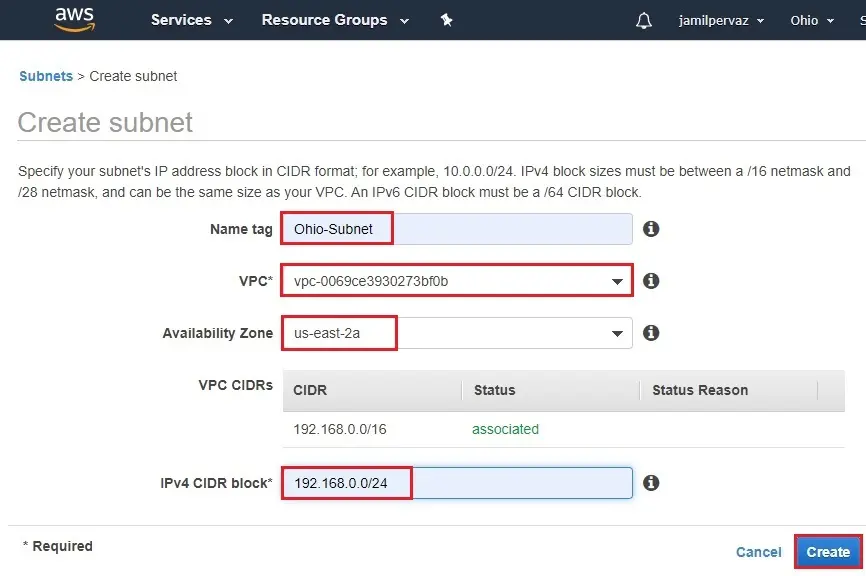
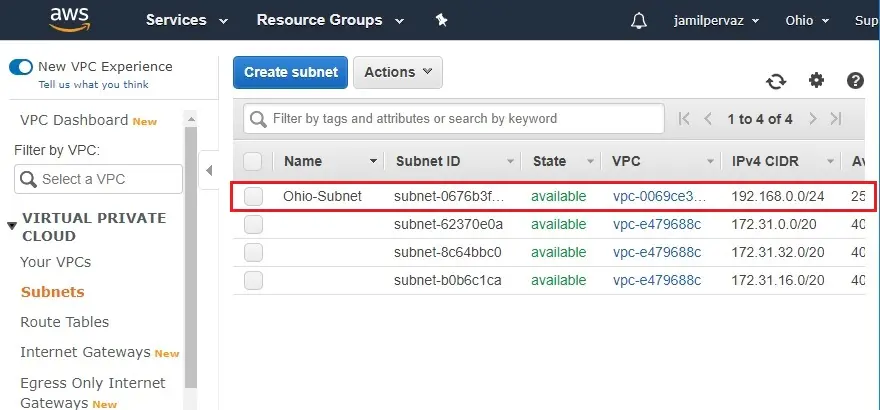
2- Name tag – Ohio-Subnet.
VPC – select the VPC-Ohio that you created earlier.
Availability Zone
IPv4 CIDR block – Type a CIDR block. For example (192.168.0.0/24)
Click Create.
3- Click close
4- Subnets successfully created.
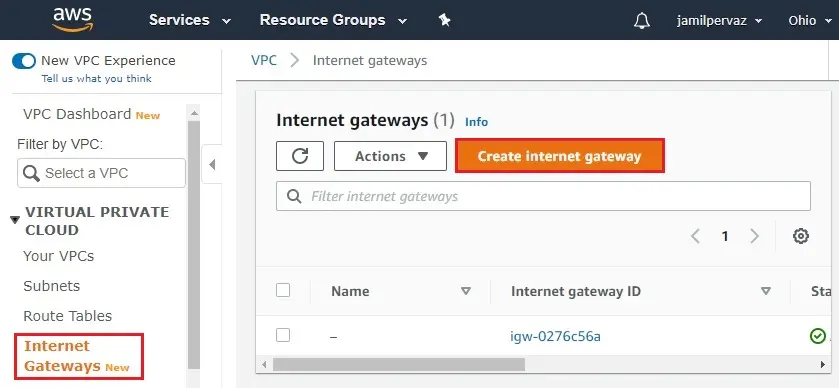
Create Internet Gateway
1- Choose Internet Gateways new and then select Create Internet Gateway.
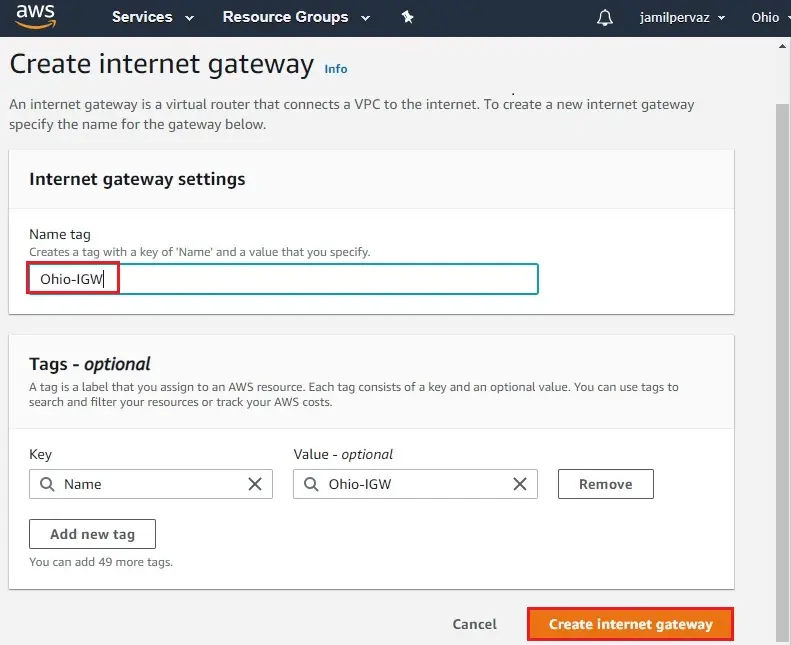
2- Enter a name (Ohio-IGW) in the Name tag text box and then click create an internet gateway.
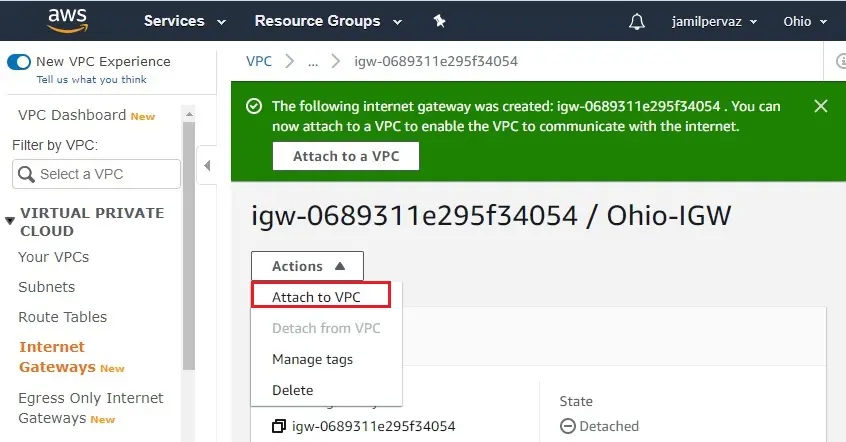
3- The internet gateway (IGW) just created is in a detached state. Now you need to attach it to the VPC.
choose the action menu select Attach to VPC.
4- Select your VPC-Ohio from the drop-down list and then click Attach internet gateway.
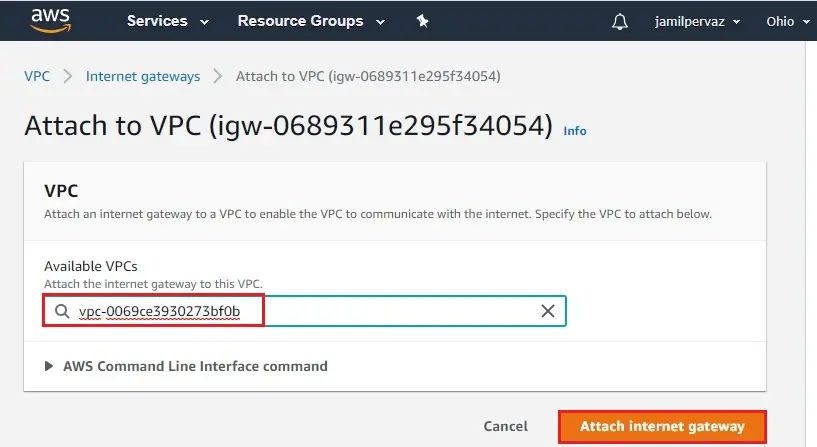
5- The internet gateway changes to attached state.
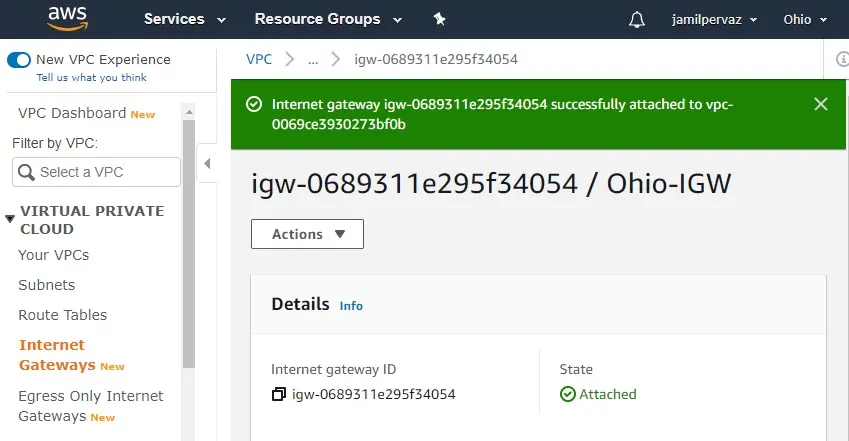
Create Route Table
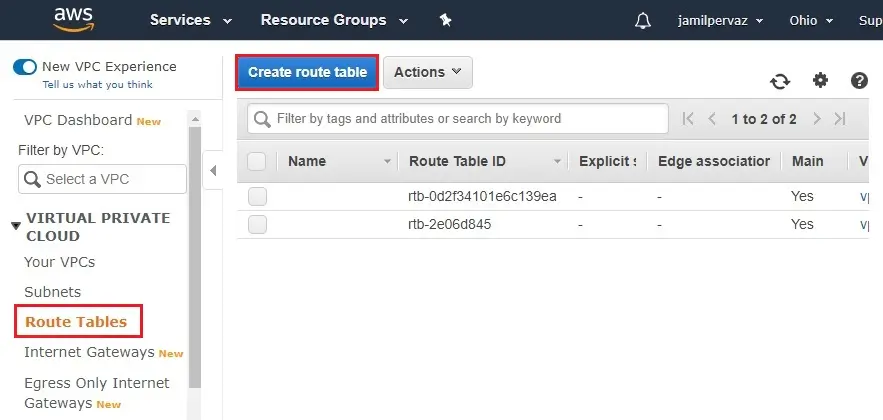
1- Select Route Tables.
Click on Create route table.
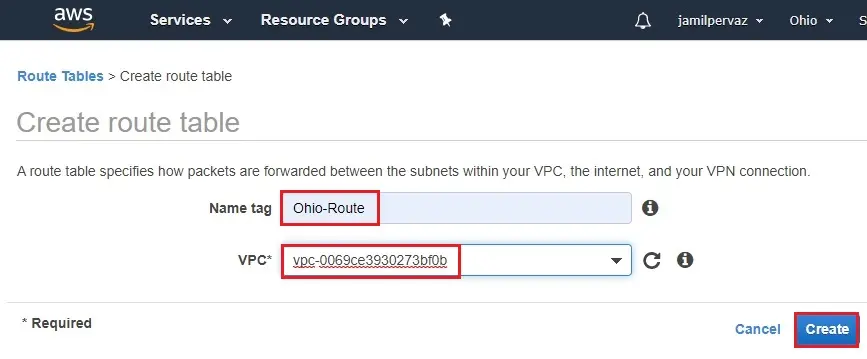
2- Name tag – Type a name for your route table (Ohio-Route).
VPC – Select your VPC-Ohio, and then select Create.
3- Click Close
Routing of public subnets
We need to configure the routing for our subnets. Enable traffic from the subnets to Internet by using the IGW (internet gateway) attached to the VPC.
4- Select Ohio-Route, Select Routes tab and then click Edit routes. Click Add route.
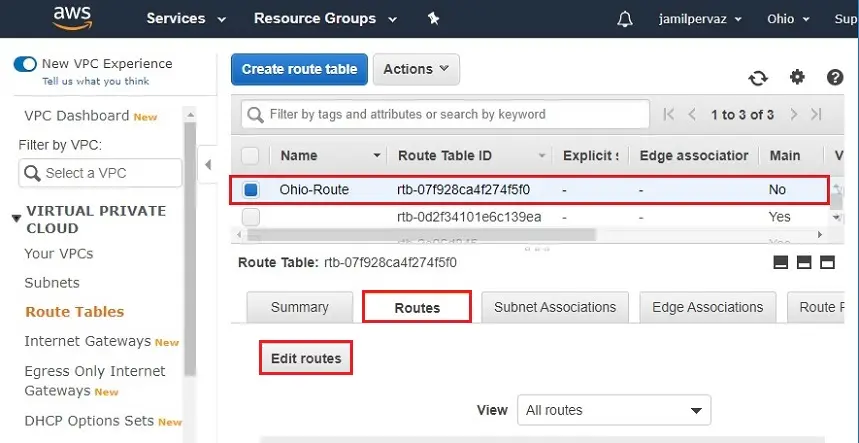
5- The traffic from the instances in the subnets intended to the Internet will be redirected to the IGW.
Reoriented to the Route Table in the Virtual Private Cloud.
Add route for the Route Table, one for the traffic to the Internet to be routed using the IGW.
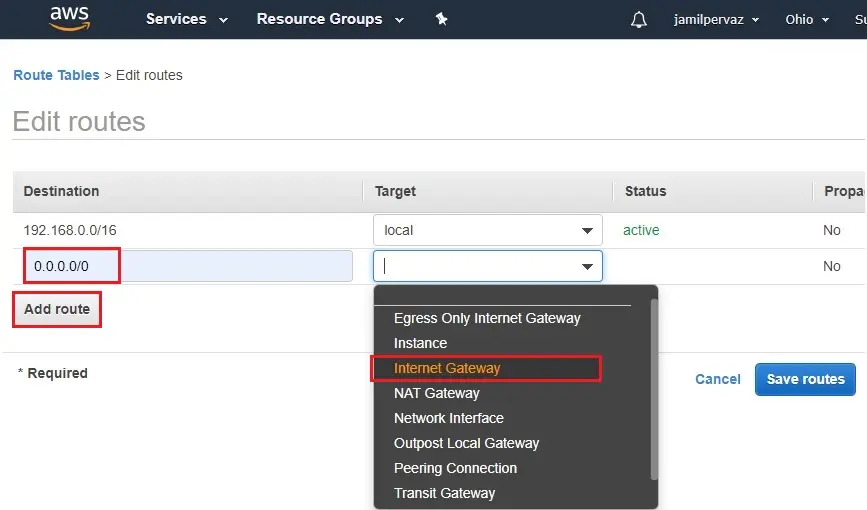
Select Add rules for destination type 0.0.0.0/0 (all packets for the internet) and for targets select the Internet Gateway.
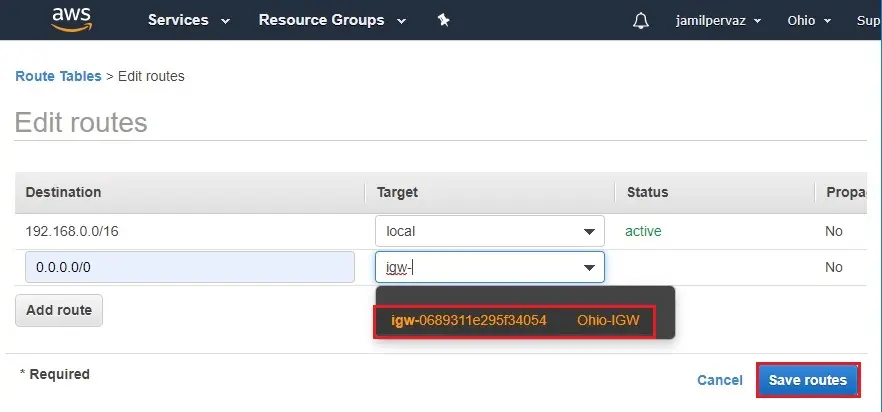
6- Select (Ohio-IGW) have created as in the earliest and then select Save routes.
7- Click close.
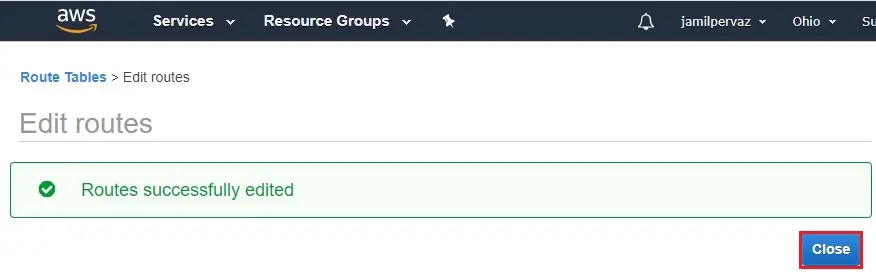
8- Successfully route edited
Choose Subnet Associations and then select Edit Subnet Associations.
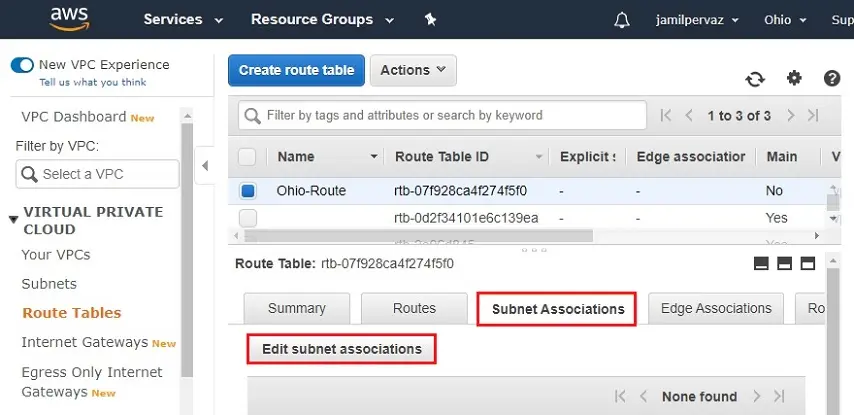
9- Select your subnet (Ohio-Subnet) and then click Save.
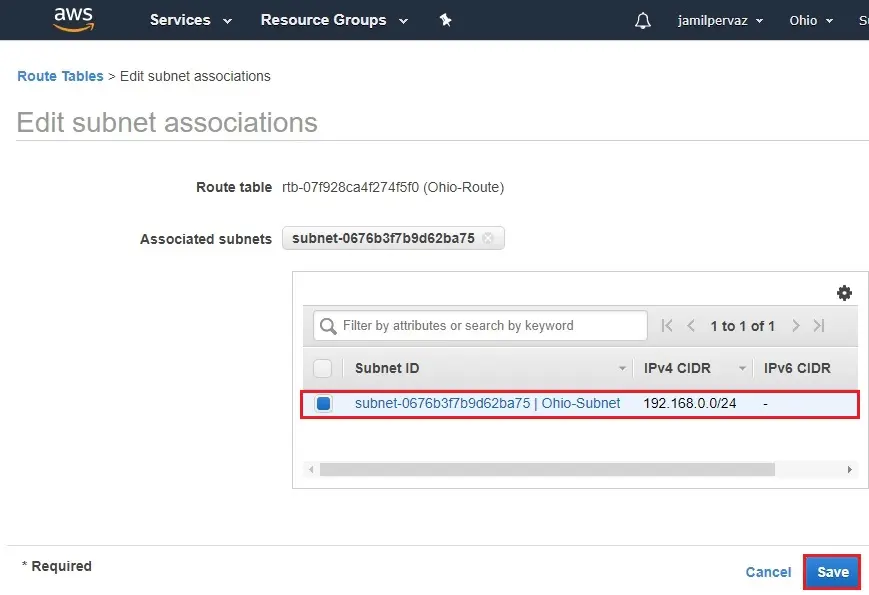
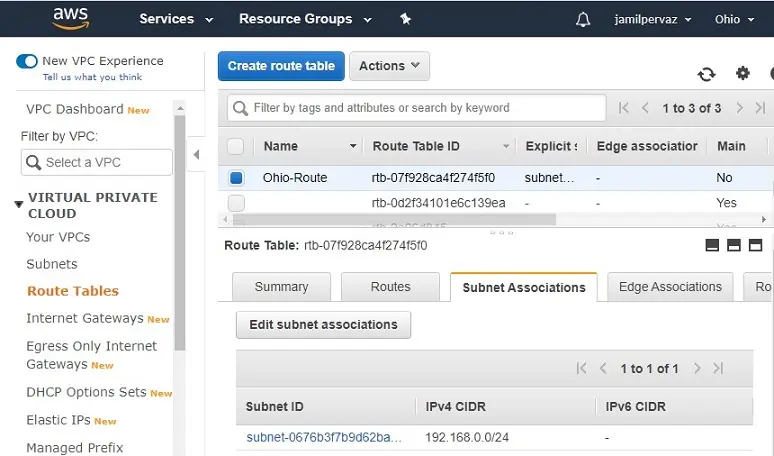
10- Successfully edit subnet associations.
Steps to create VPC Peering connection across region in AWS
How to Create VPC Tokyo
1- Login to AWS account and choose the AWS Services tab and then select VPC under Networking & Content Delivery.
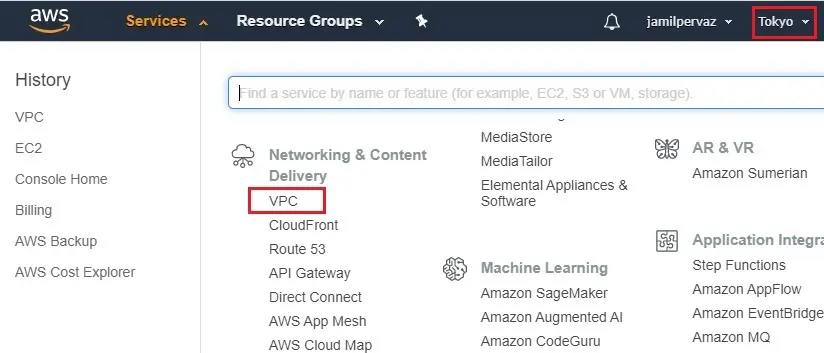
2- Under Virtual Private Cloud select Your VPCs
Click on Create VPC.
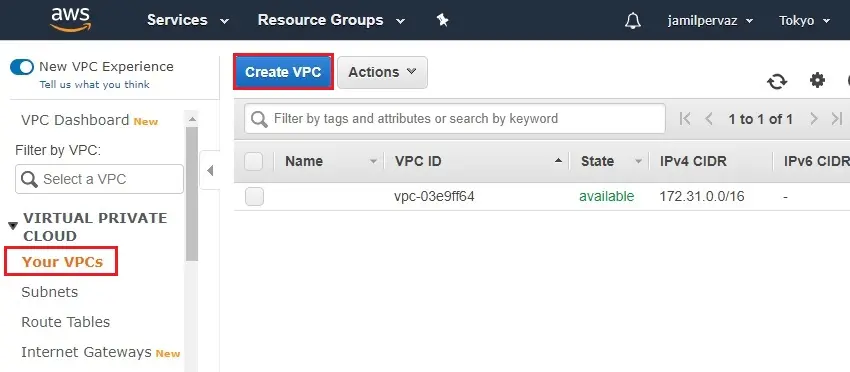
3- Create VPC wizard,
Name tag – VPC-Tokyo.
IPv4 CIDR block – 10.0.0.0/16.
Tenancy – default
Click Create
4- Click close
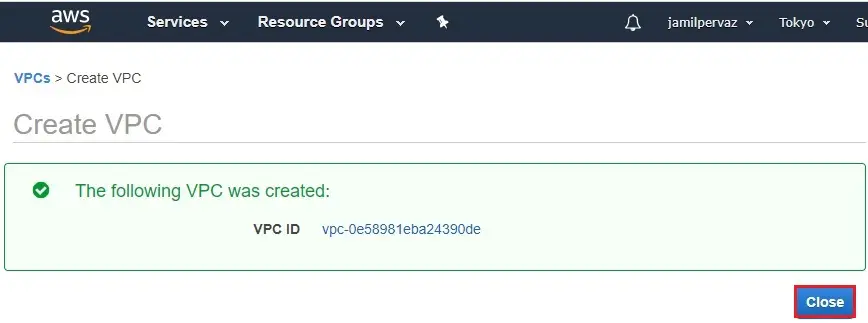
5- Now you can see VPC successfully created in Tokyo Region.
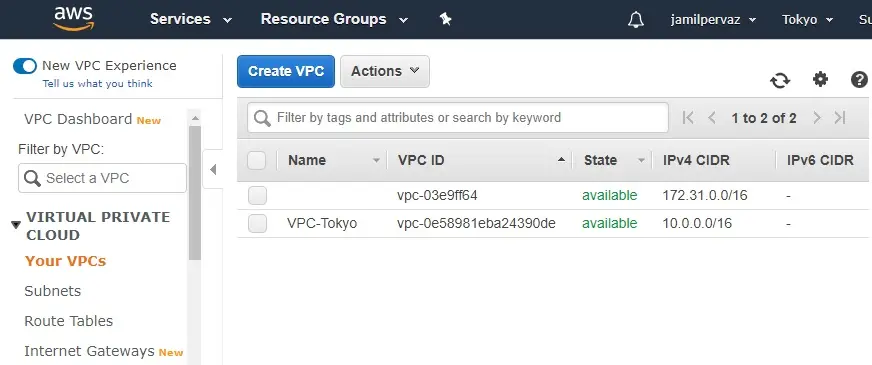
Create Subnet
1- Select Subnets.
Choose Create Subnet.
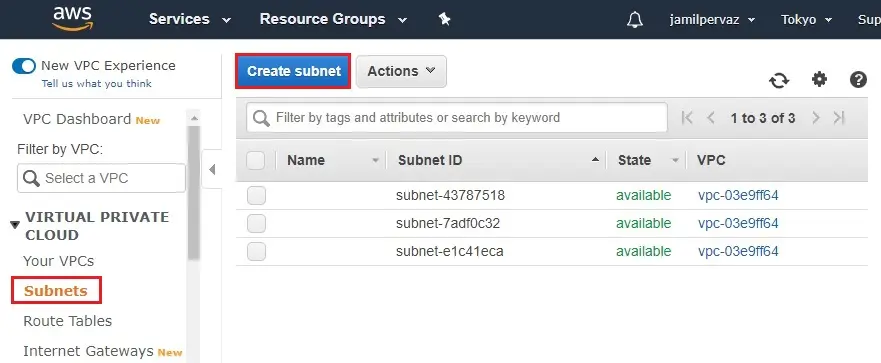
2- Name tag – Tokyo-Subnet.
VPC – select the VPC-Tokyo that you created earlier.
Availability Zone
IPv4 CIDR block – Type CIDR block. For example (10.0.0.0/24)
Click Create.
3- Click close
4- Subnets successfully created.
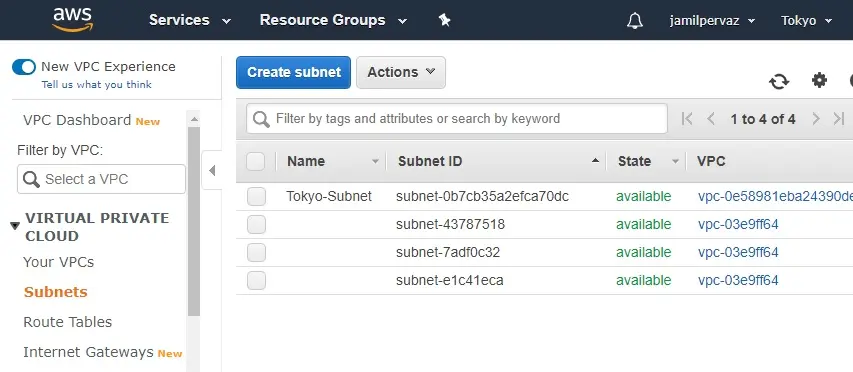
Create Internet Gateway
1- Choose Internet Gateways new option and then click Create Internet Gateway.
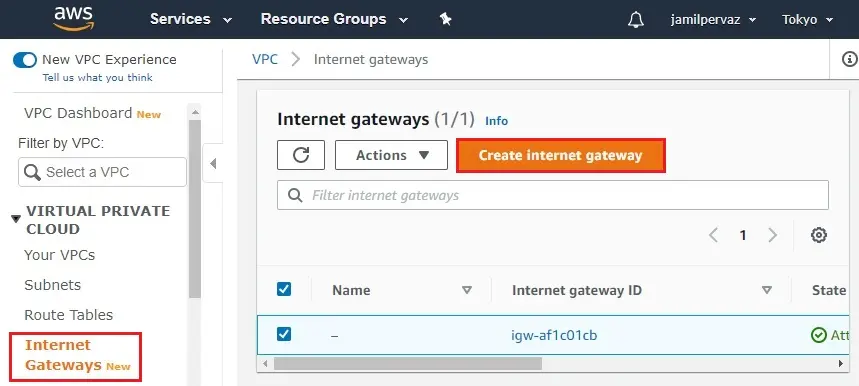
2- Enter a name (Tokyo-IGW) in the Name tag text box and then click create internet gateway.
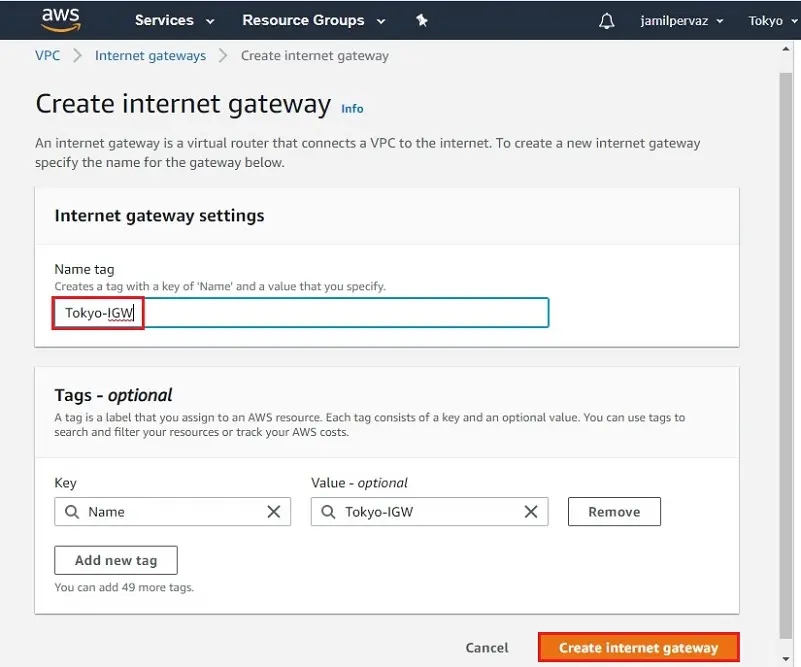
3- The IGW just created is in a detached state. Now we need to attach it to you VPC.
In the action menu select Attach to VPC.
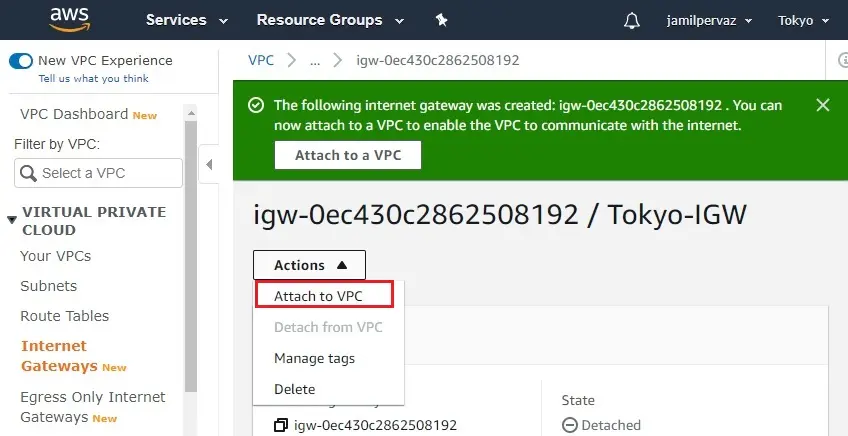
4- Select your VPC-Tokyo from the drop-down list and then click Attach internet gateway.
5- The internet gateway changes to attached state.
Create Route Table
1- Select Route Tables.
Click on Create route table.
2- Name tag – Type a name for your route table (Tokyo-Route).
VPC – Select your VPC-Tokyo, and then select Create.
3- Click Close.
Routing of public subnets
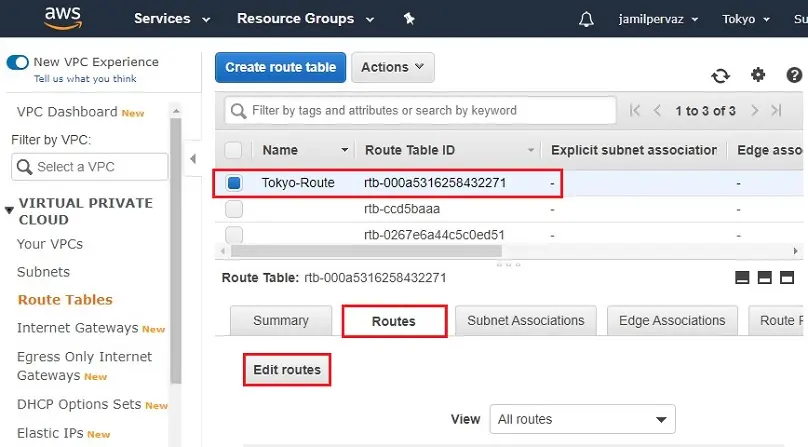
4- We want to configure the routing for the subnets. Enable traffic from the subnets to Internet by using the IGW attached to the VPC.
Select Ohio-Route, Select Routes tab and then click Edit routes.
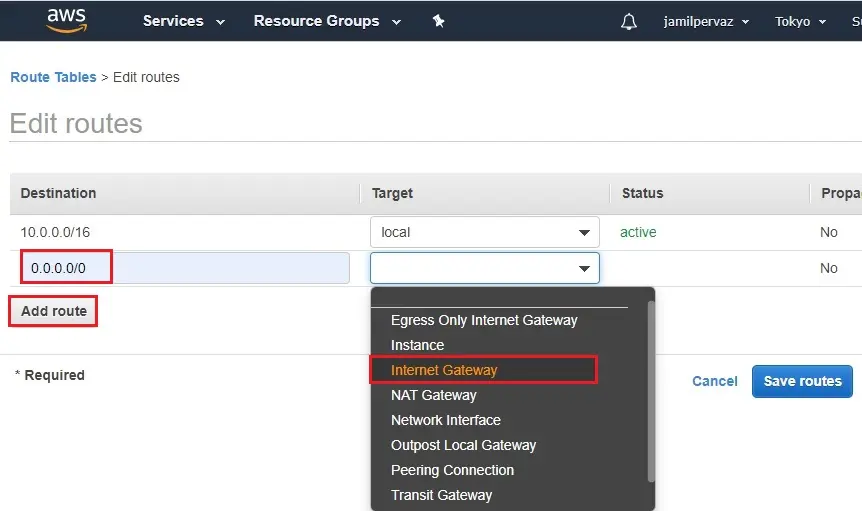
5- Now traffic from AWS instances in the subnets predestined to the Internet will be redirected to the Internet Gateway.
Then you can redirect to the Route Table in the Virtual Private Cloud.
Add route for the Route Table, 1 for the traffic to the Internet to be routed using the IGW.
Choose Add rules button for destination enter 0.0.0.0/0 (all packets for the internet) and then select the Internet Gateway for targets.
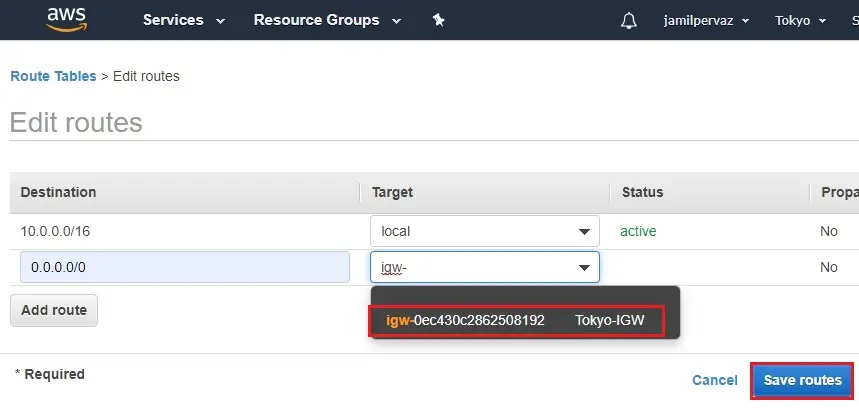
6- Select (Tokyo-IGW) have created as in the earliest and then select save routes.
7- Click close.
8- Successfully route edited
Choose Subnet Associations and then choose Edit Subnet associations.
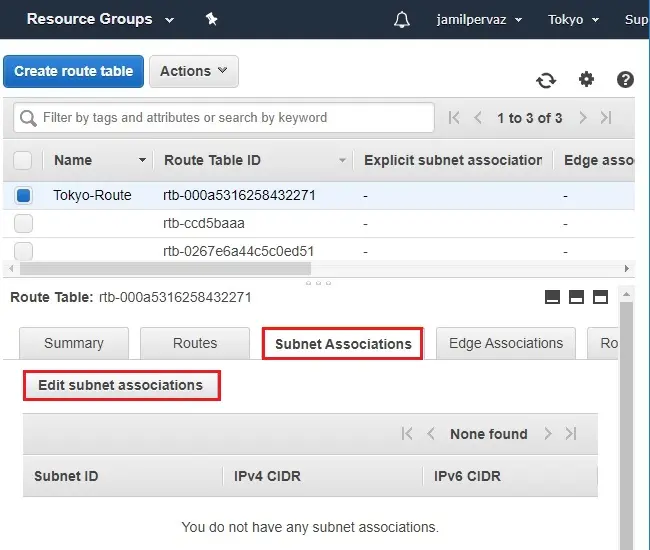
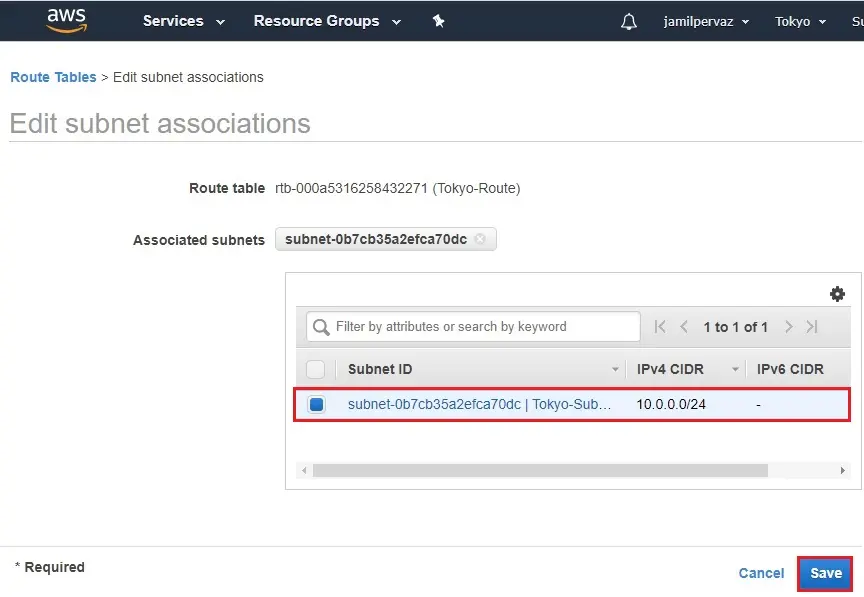
9- Select your subnet (Tokyo-Subnet) and then click Save.
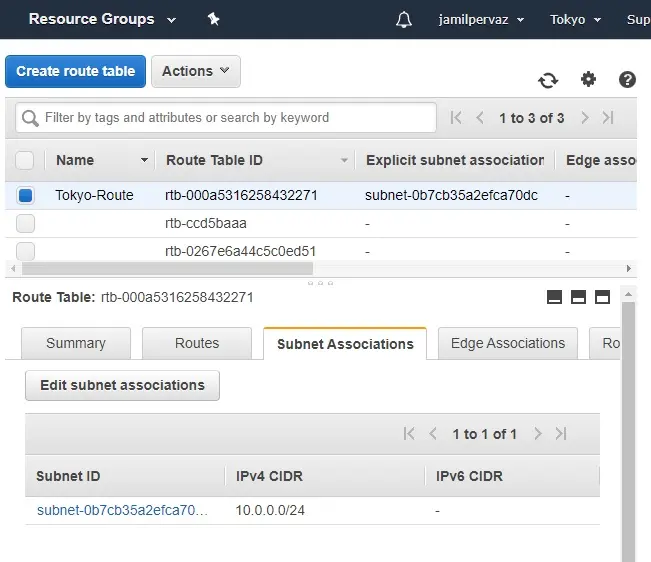
10- Successfully edit subnet associations.
Creating VPC Peering Connection
1- Under the virtual private cloud, select peering connections.
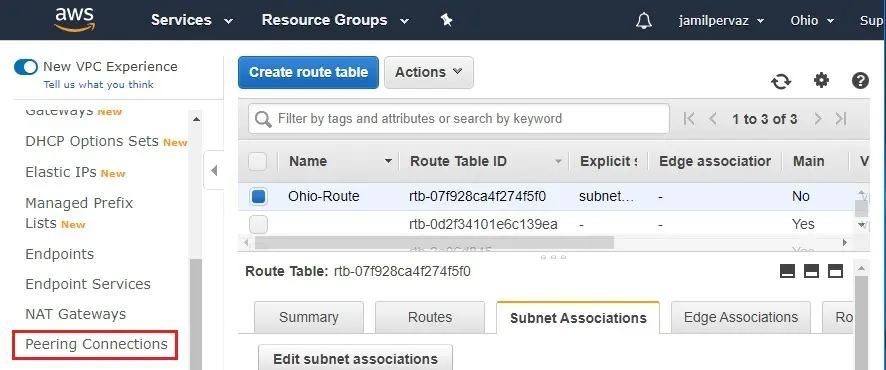
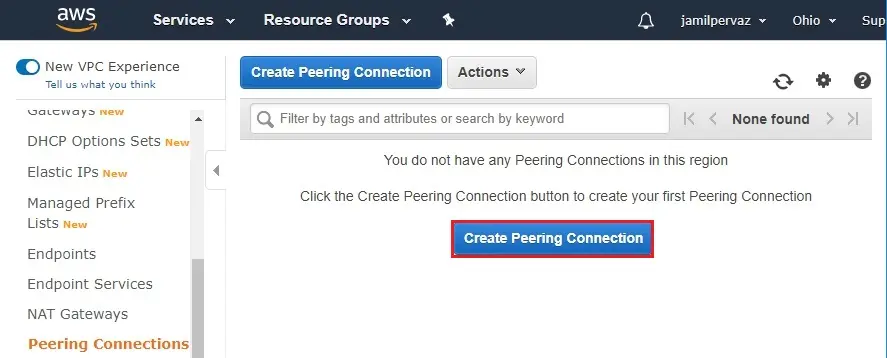
2- Click on create peering connection button.
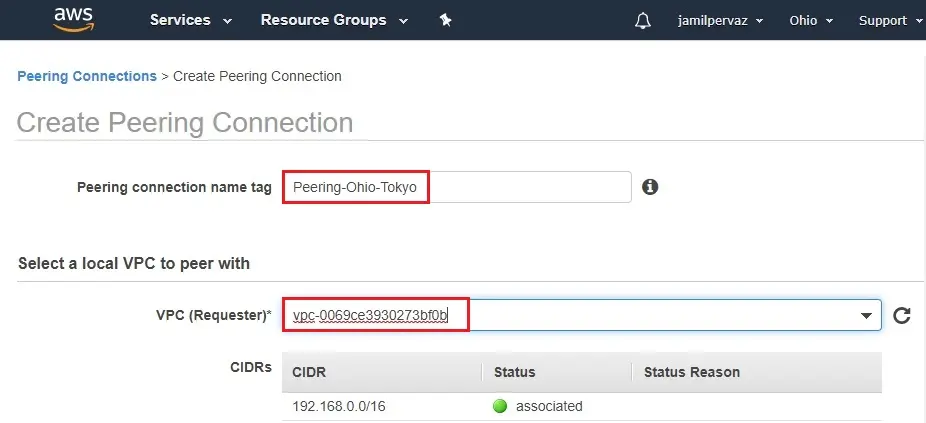
3- Provide a name for the peering connection (Peering-Ohio-Tokyo) and select the local VPC (VPC-Ohio) from the drop-down list.
Go to your Tokyo region
4- Select Your VPCs
Select Description and then copy VPC ID
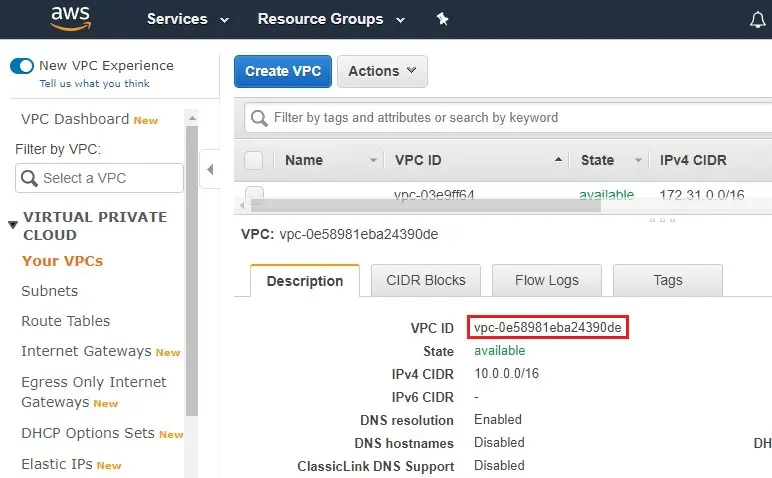
We have created the two VPC’s indifferent under the same AWS account.
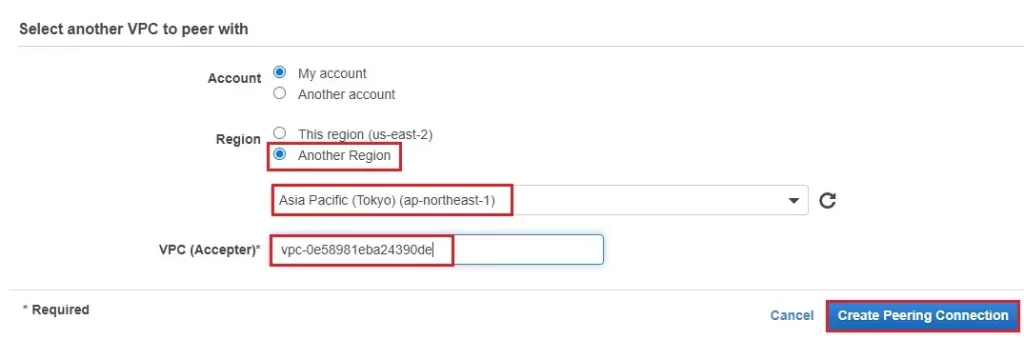
5- Select another VPN to peer with
Select the Account as My account
Region – Select Another region
Select other region (in this article I have other region Tokyo)
VPC (Accepter) – Paste VPC ID (Tokyo) we have copied earlier
After selecting the VPC (Requester) and then VPC (Accepter) click create peering connection.
6- Click OK.
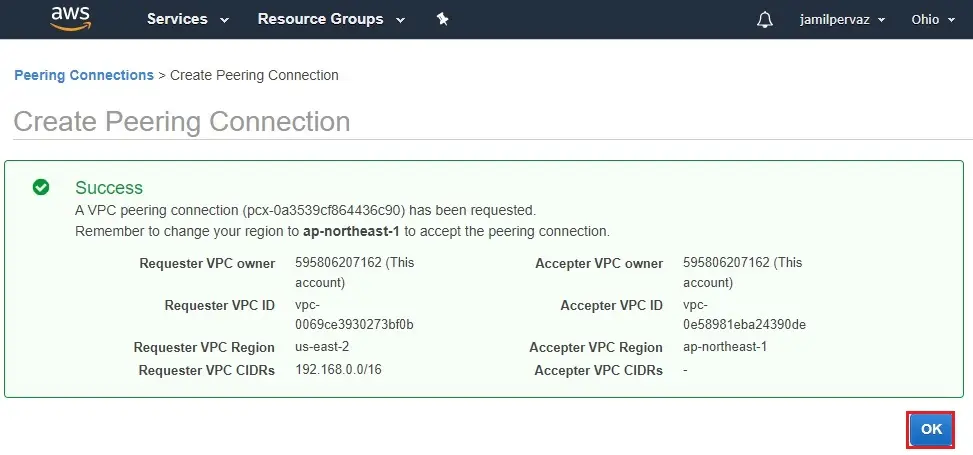
7- Now peering connection is created (between Ohio and Tokyo) and in pending status.
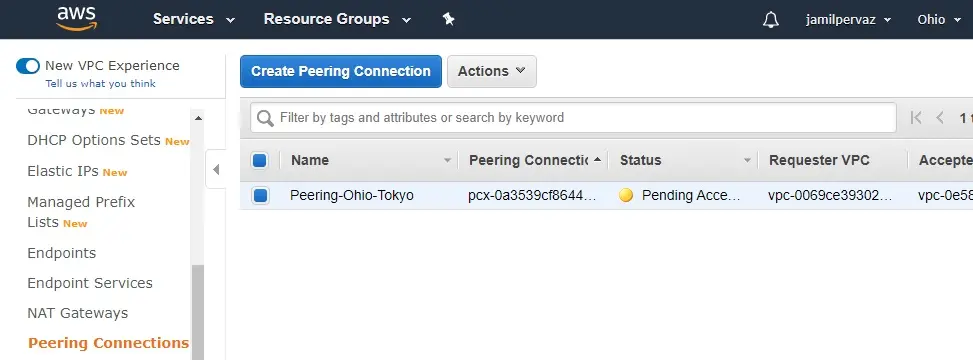
Accepting Connection
8- Go to your other region (Tokyo).
Select Peering Connection
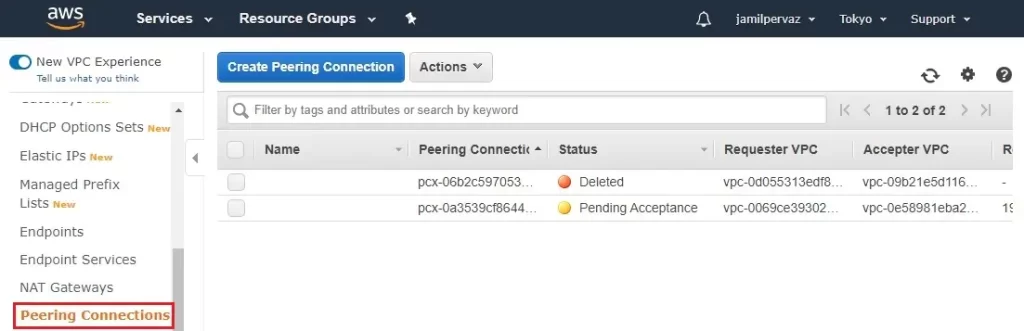
9- Click on Action menu and then click accept request.
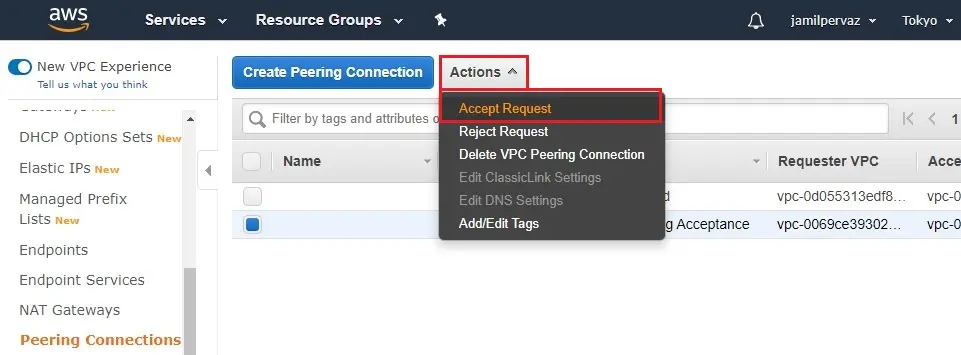
10- Click on the Yes, Accept button.
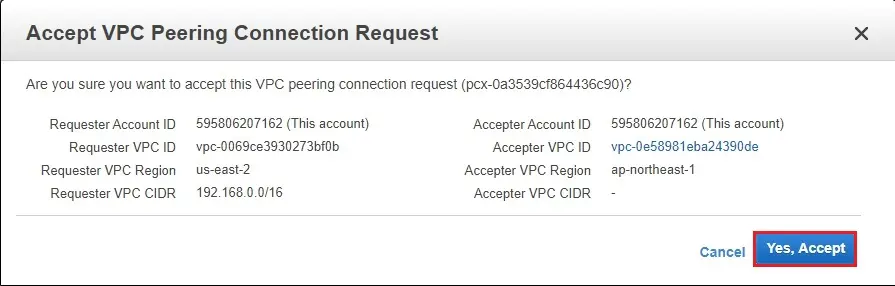
11- VPC peering connection has been established successfully.
12- Now peering connection is in active status (Tokyo).
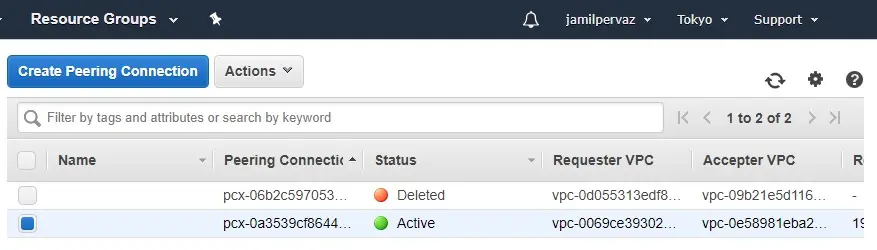
13- Now peering connection is in active status (Ohio).
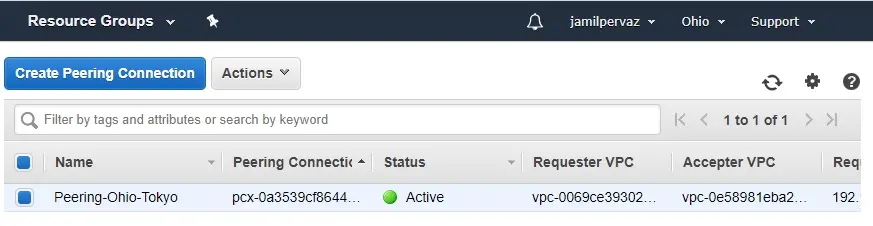
Updating the Routing Tables in Ohio Region
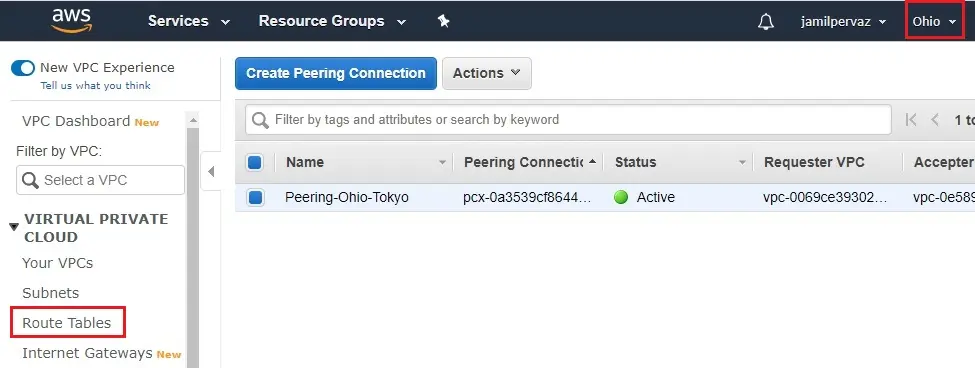
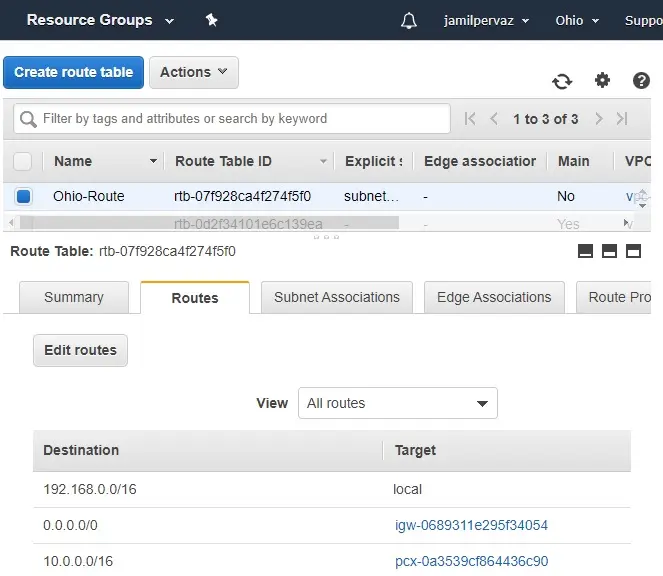
1- Go to Ohio region and access VPC dashboard. Click on the Routing table’s link.
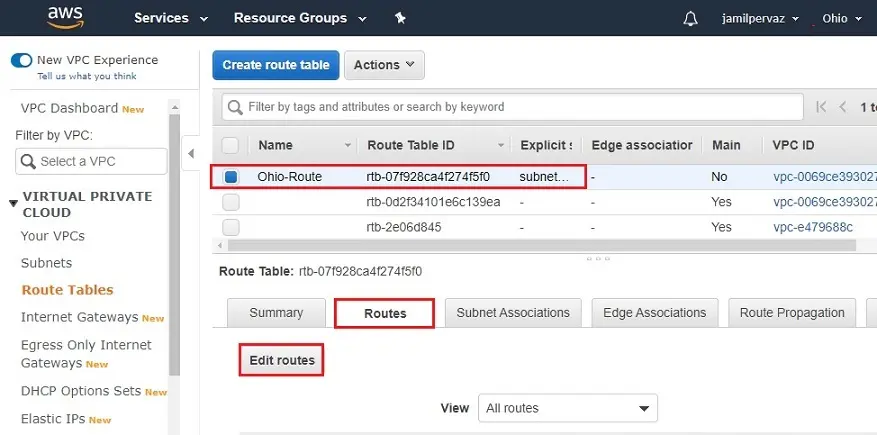
2- Select Ohio-Route, Select Routes tab and then click Edit routes.
3- Add the new route entry for Tokyo VPC Network range.
We use 10.0.0.0/16 range as the VPC network in the Tokyo region.
choose the peering connection as a target from the drop-down list.
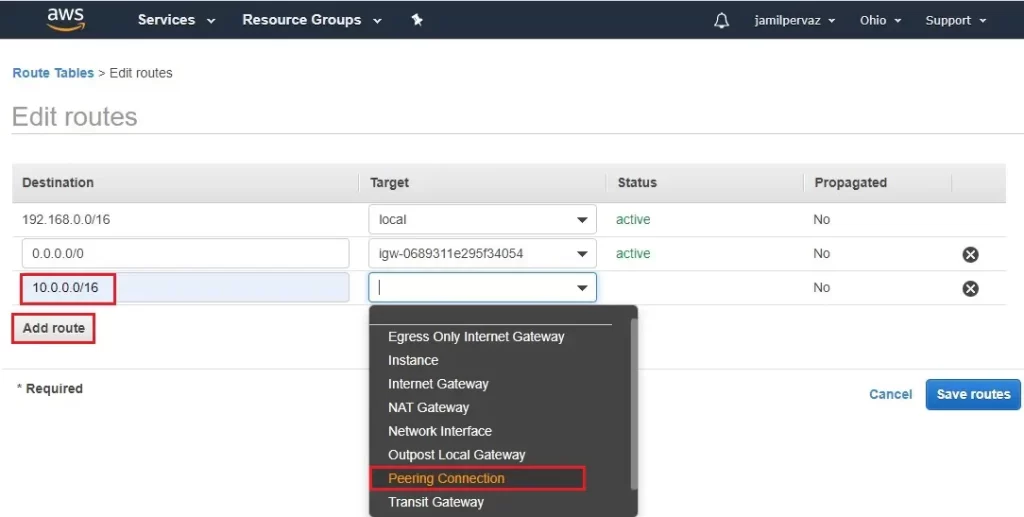
4- Select peering-Ohio-Tokyo and then click save routes.
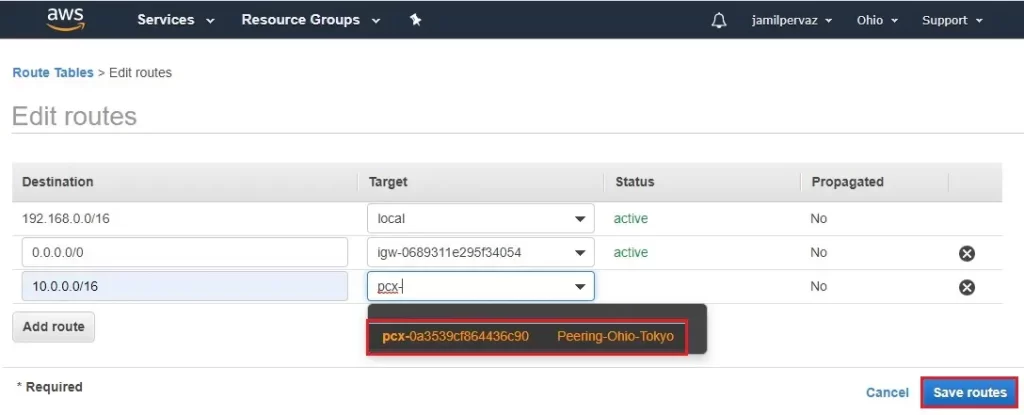
5- Click close
6- Successfully route edited.
Updating the Routing Tables in Tokyo Region
1- Go to Tokyo region and access VPC dashboard. Click on the Routing tables.
Select Tokyo-Route, select Routes tab and click on edit routes.
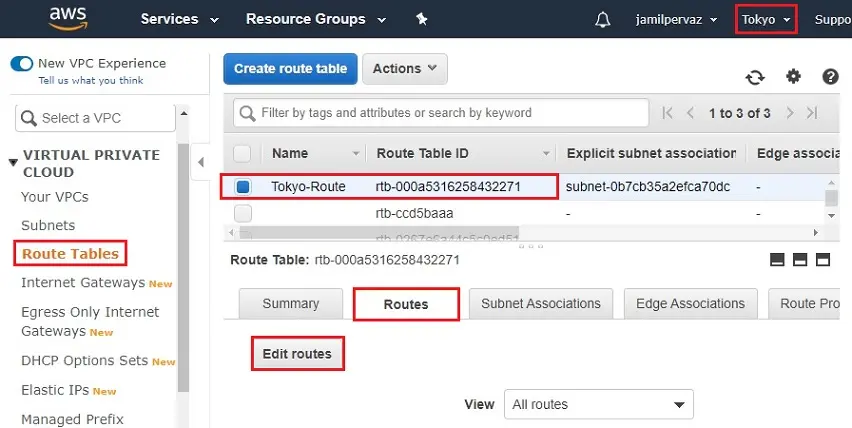
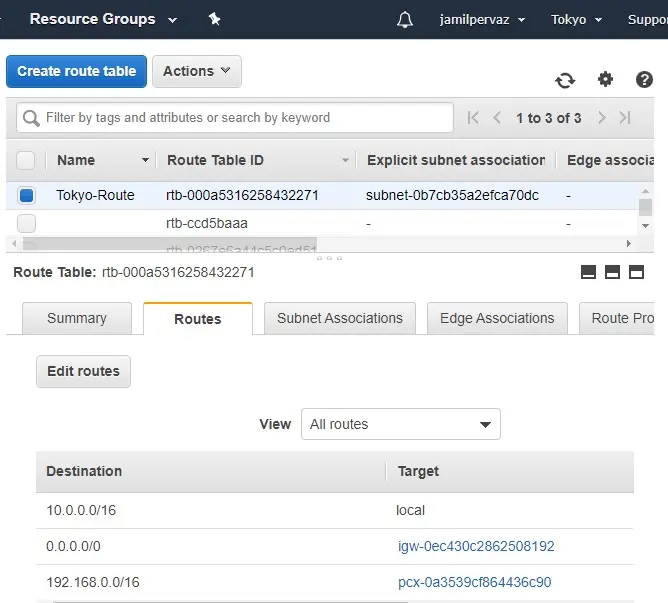
2- Now, add the Ohio region VPC network in Tokyo Routing Table. We use 192.168.0.0/16 range as the VPC network in Ohio region.
Select Peering Connection
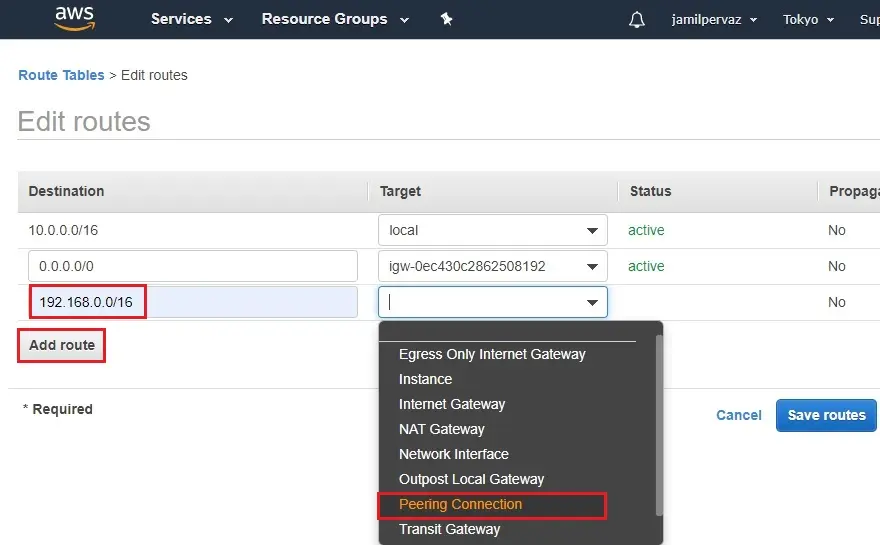
3- Select peering-Ohio-Tokyo and then click save routes.
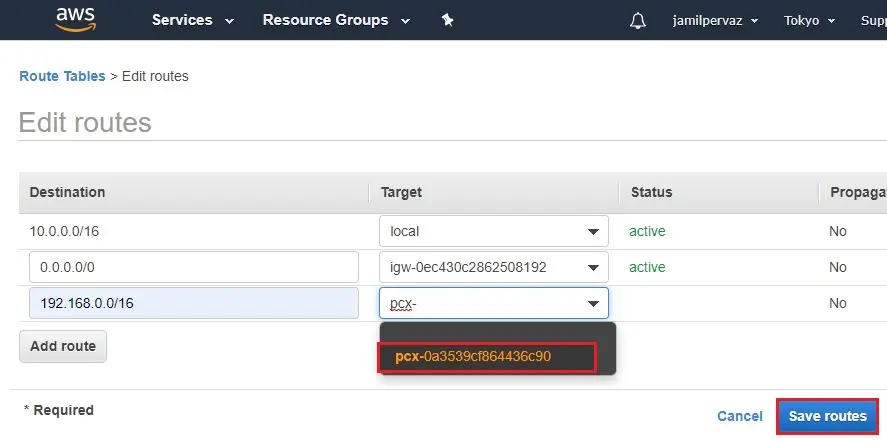
4- Click close
5- Successfully route edited
Create Instance (Tokyo Region)
1- Choose service tab and then choose EC2 under compute.
2- Choose instance on your left side and then select Launch Instance button.
3- Choose Microsoft Windows Server 2019.
4- Choose the instance type as per your requirements.
Click Next : Configure Instance details.
5- Network – select VPC (VPC1-Tokyo).
Subnets – select Tokyo-Subnet.
Auto Assign Public IP – select Enable.
Click on Next : Add Storage.
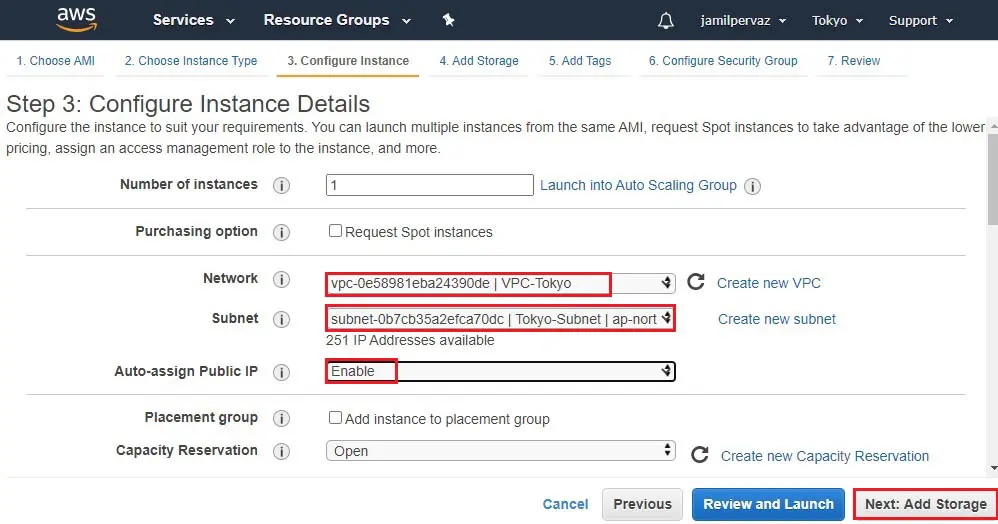
6- Click Next : Add Tags.
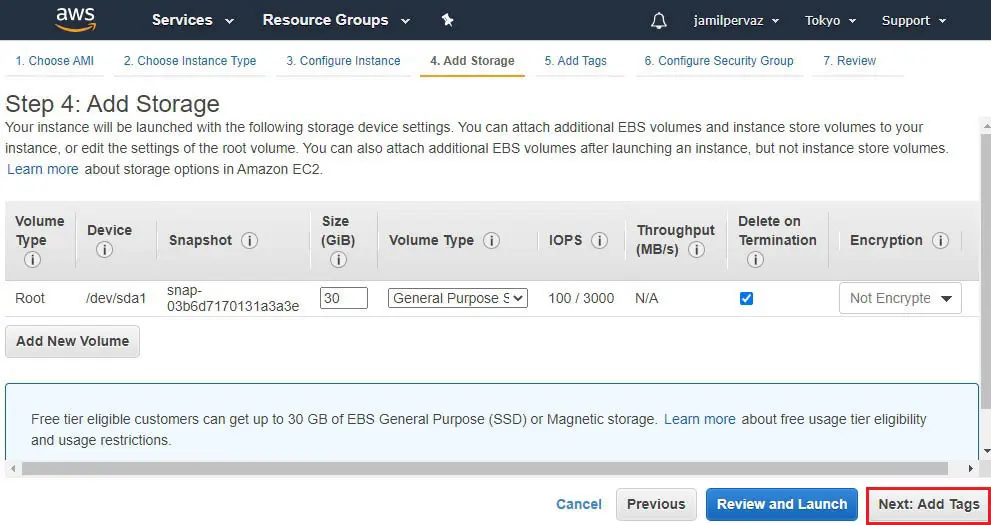
7- Here we can tagged the instance (Tokyo-Instance)
Click on Next : Configure Security Groups
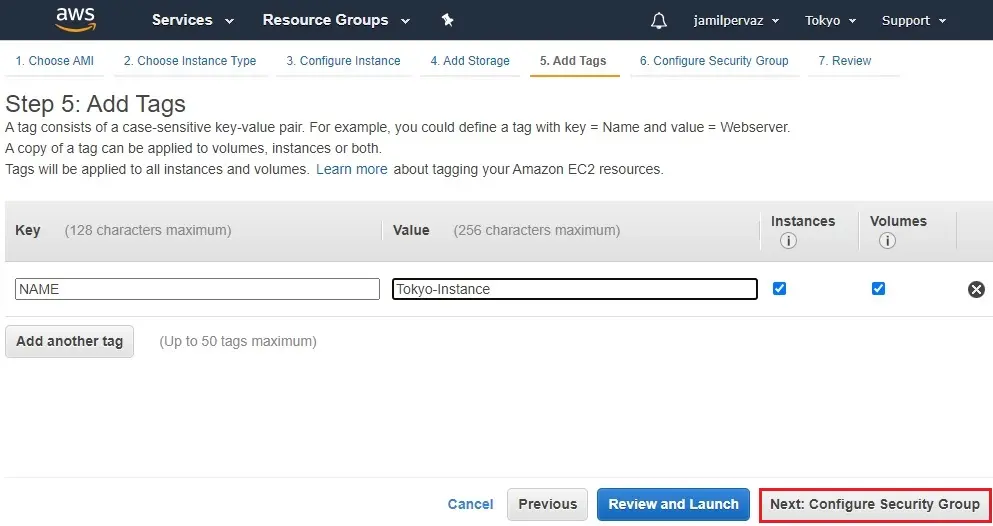
8- Create new Security Group.
Security group name – Tokyo-Security
Choose Protocols RDP, ALL ICMP – Ipv4, choose Source Anywhere
Click on Review and then Launch
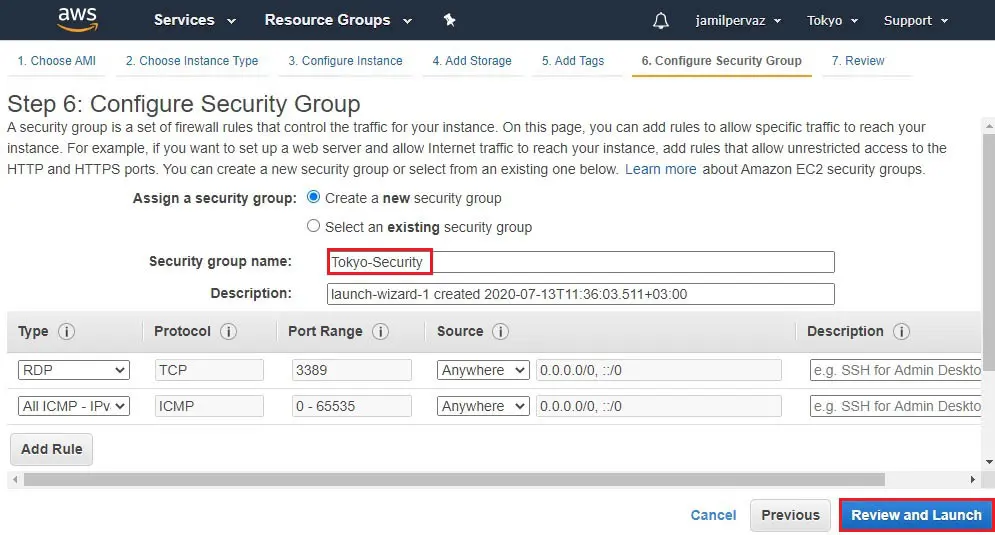
9- Review instance details and then click launch.
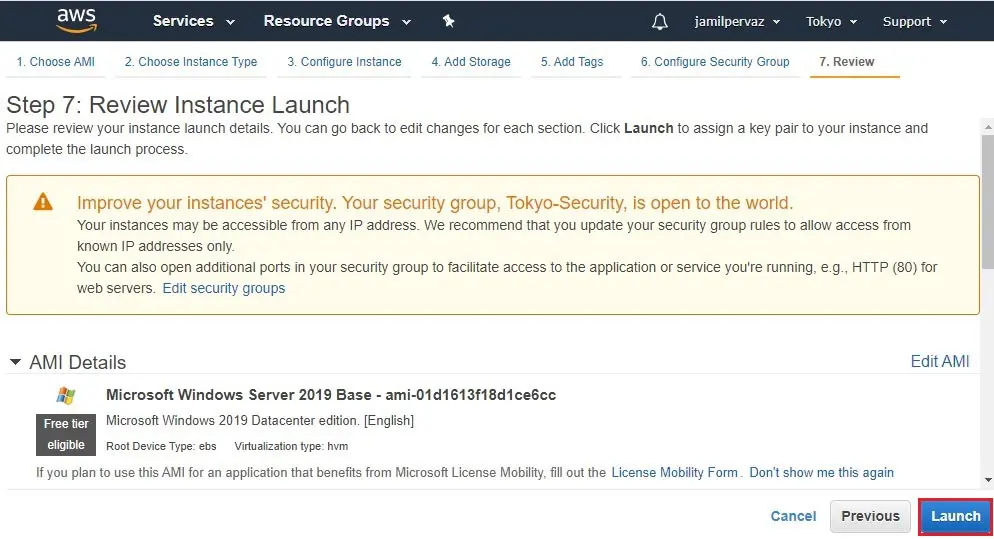
10- Choose Create a new key pair
Type a name of your key (tokyo-ohio-peering)
Click the download key pair button and then save it in your secured folder
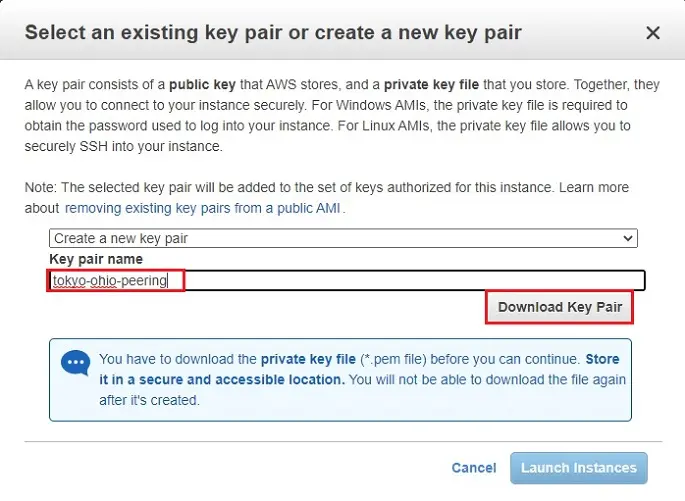
11- After downloading and saving your key pair, click launch instance.
12- Instance created.
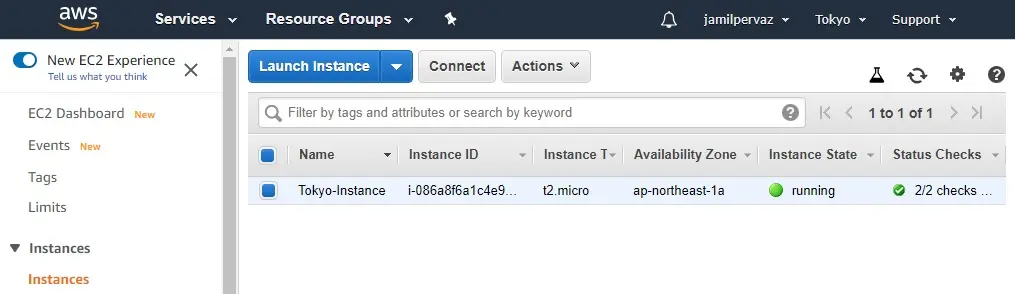
Create Instance (Ohio Region)
1- Click on service tab and then select EC2 under compute.
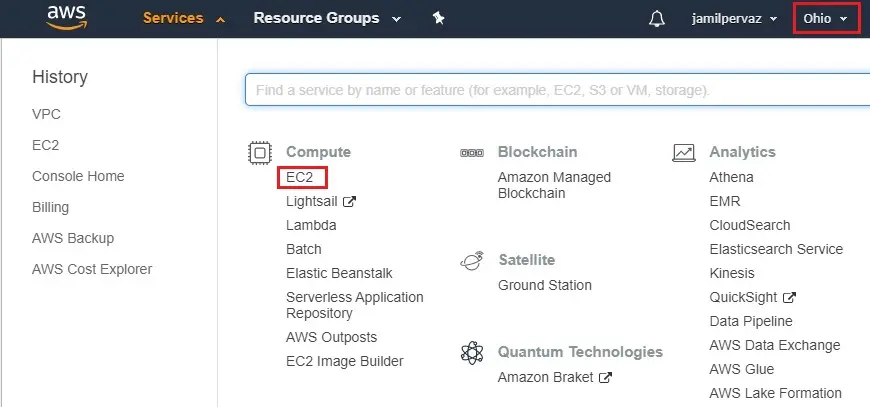
2- Select instance tab and then click on Launch Instance button.
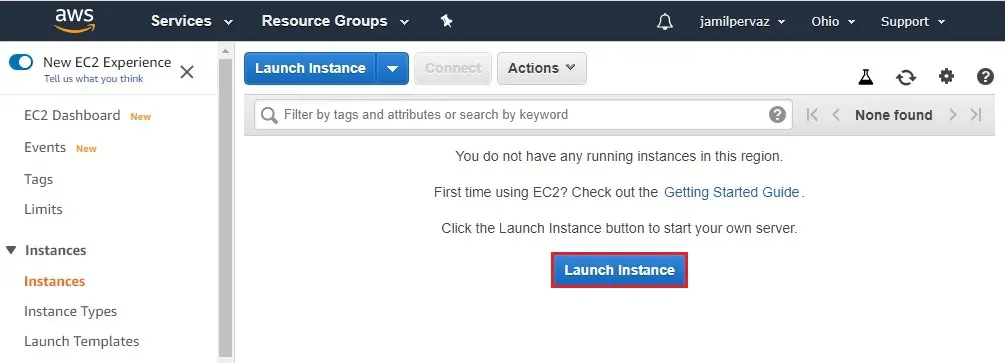
3- Select Microsoft Windows Server 2019.
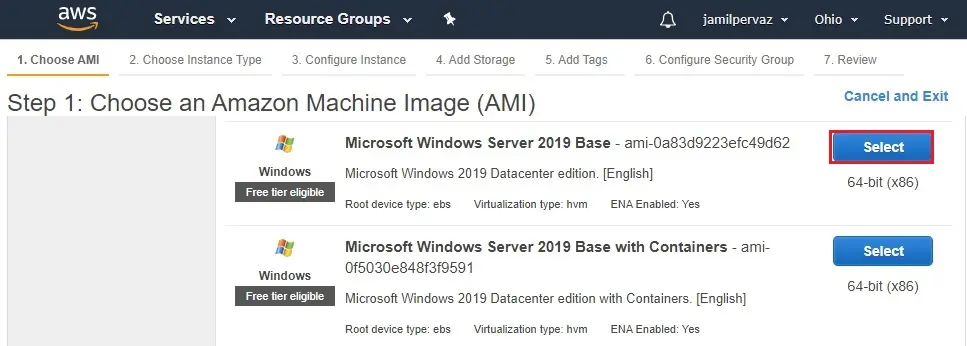
4- Click Next : Configure Instance details.
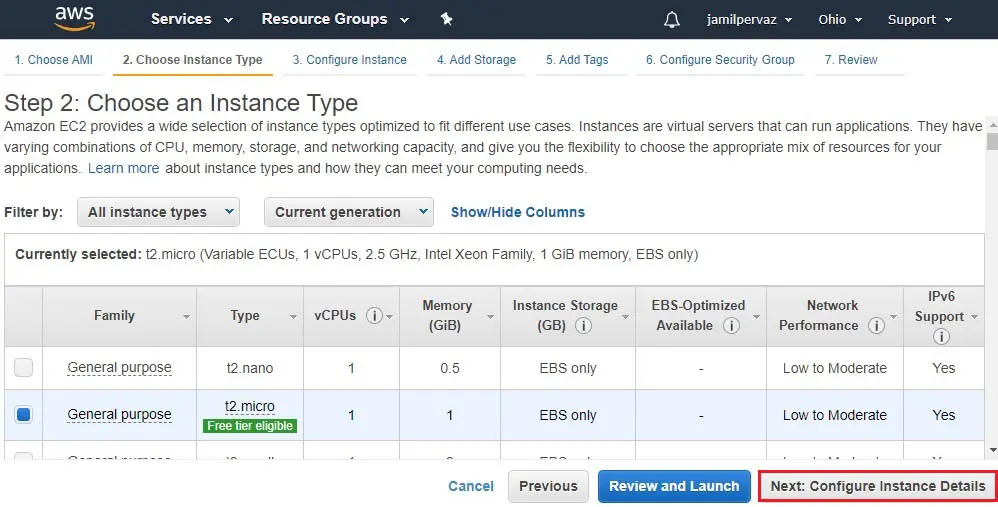
5- Network – select VPC (VPC-Ohio).
Subnets – select Ohio-Subnet.
Auto Assign Public IP – select Enable.
Click on Next : Add Storage.
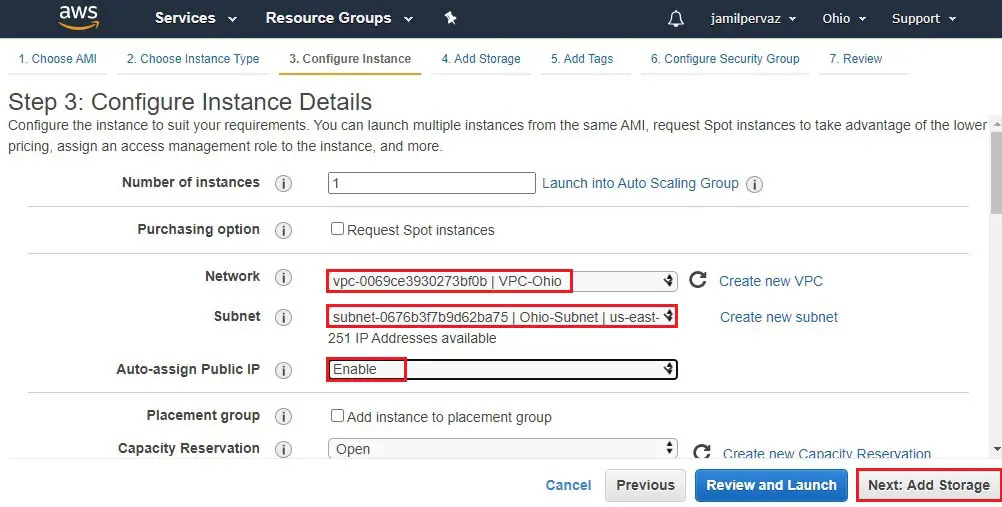
6- Click Next : Add Tags.
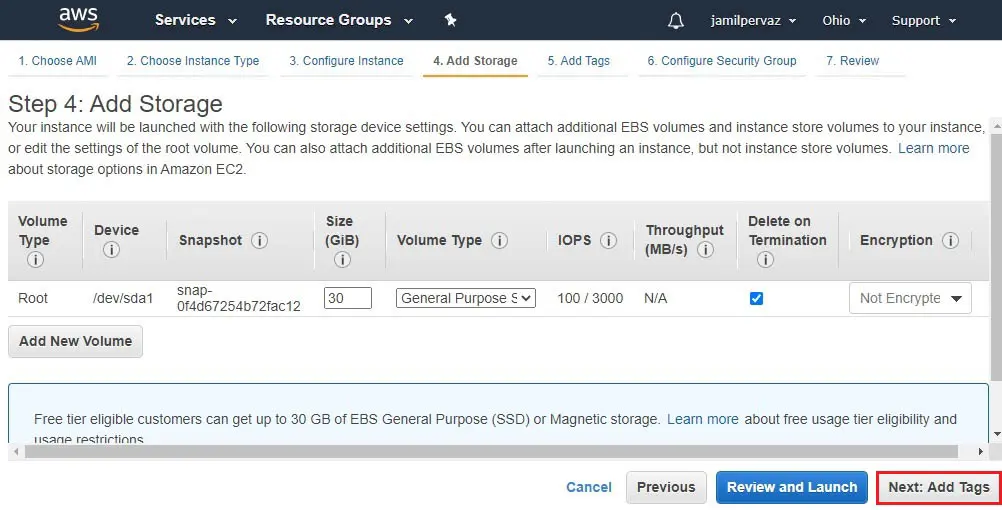
Here we have tagged the instance (Ohio-Instance)
7- Click on Next : Configure Security Groups.
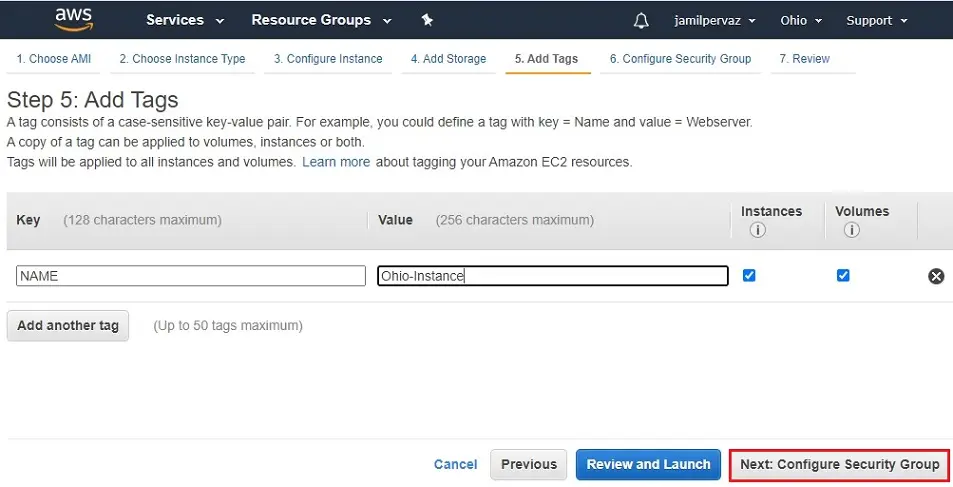
8- Create a new Security Group.
Security group name – Ohio-Security
Protocols RDP, ALL ICMP – Ipv4, choose Source Anywhere
Click on Review and Launch
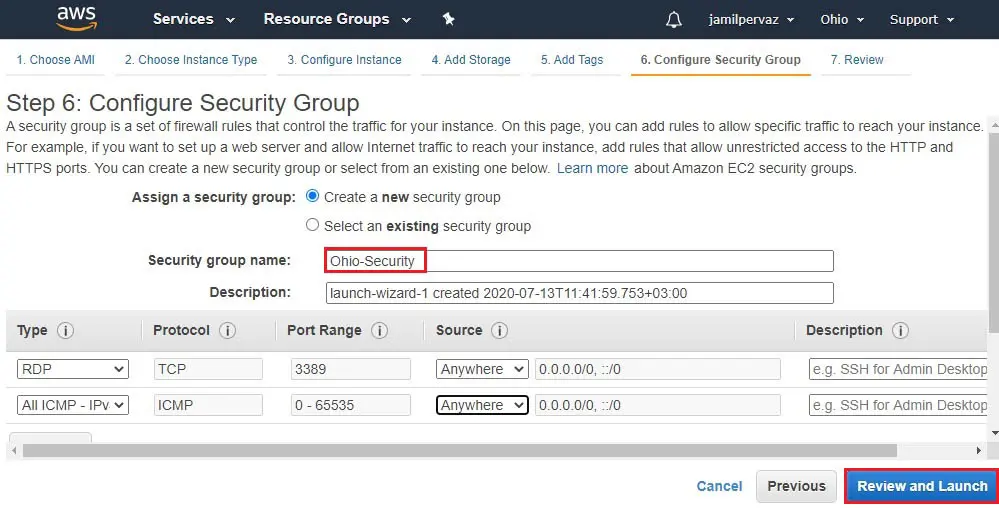
9- Review details and then click launch.
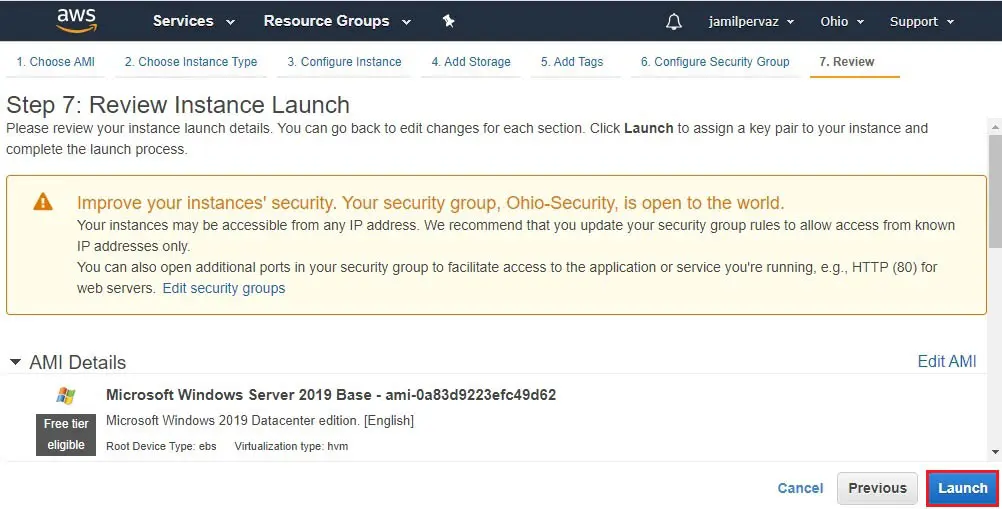
10- Select Create a new key pair
Type a name to your key (Ohio-Tokyo-Peering)
Click download key pair button and save it to secured folder
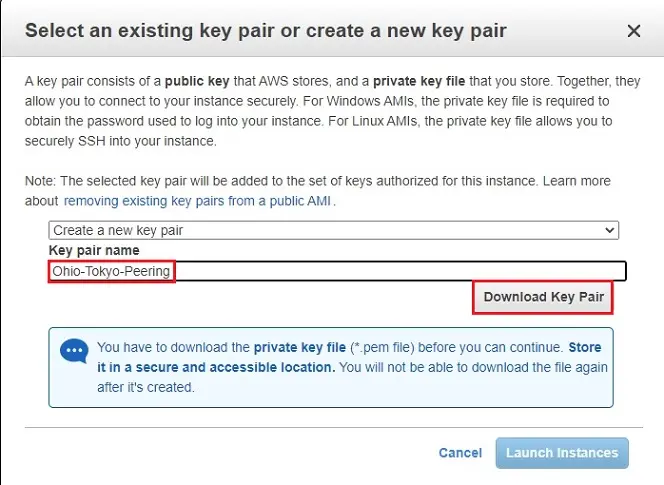
11- After downloading key pair and saving it, click launch instance.
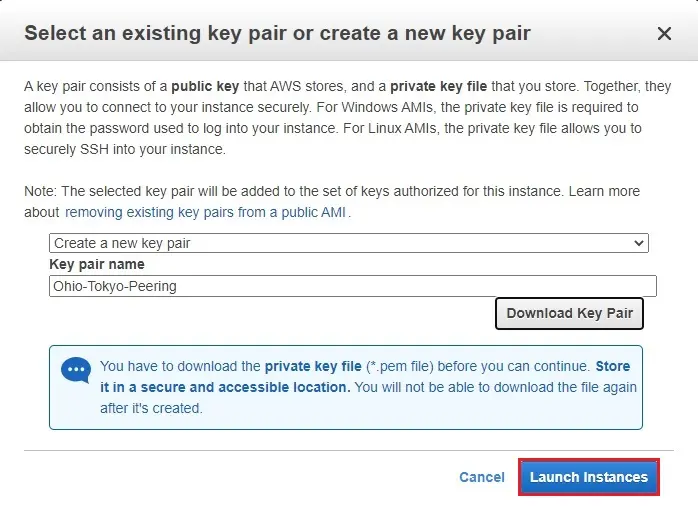
12- Ohio-Instance successfully created.
Testing VPC Peering Connection
1- Select Tokyo-Instance (Tokyo Region) and then click connect.
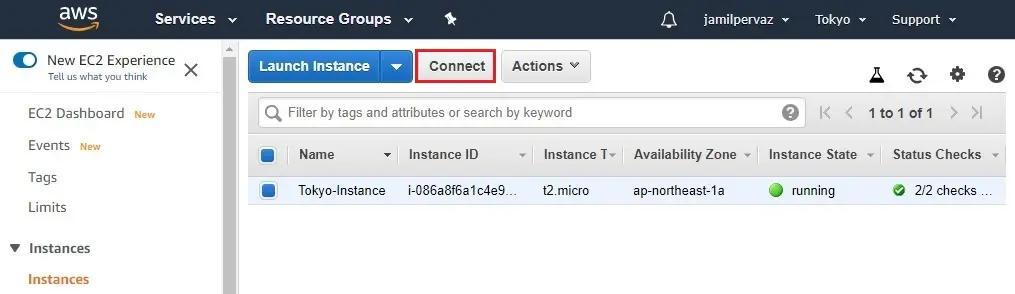
2- Select Get Password.
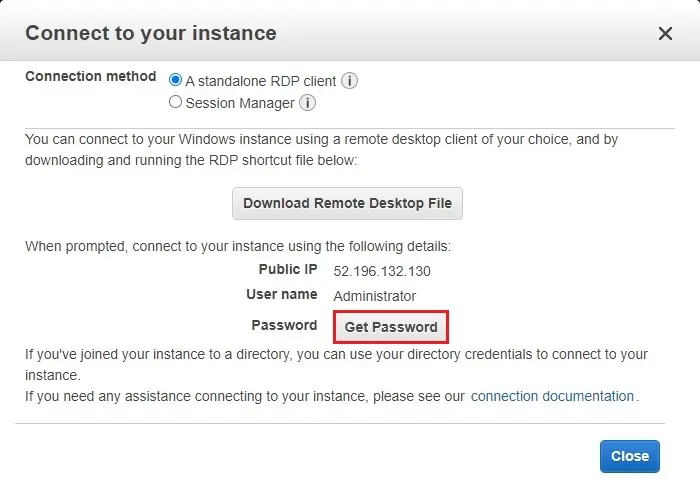
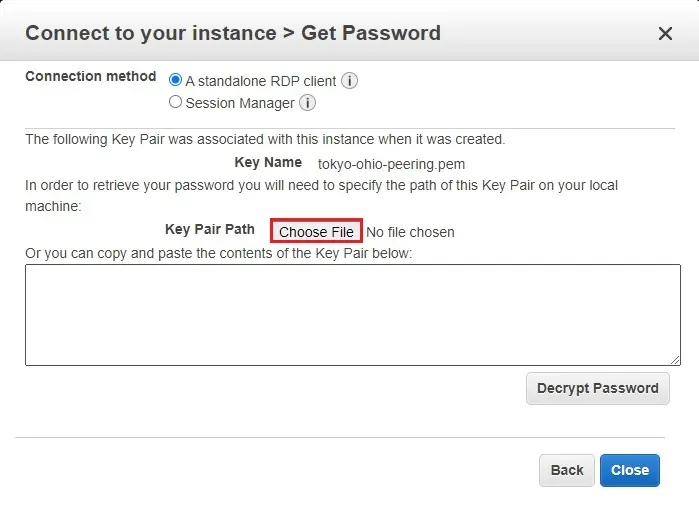
3- Select choose file and select your key pair and then click decrypt password.
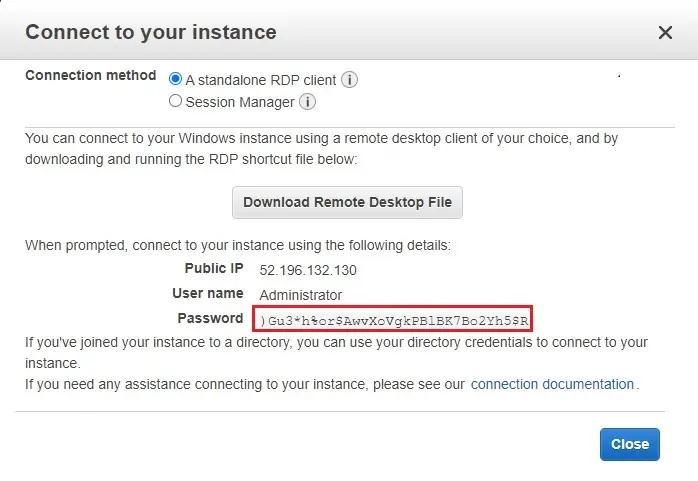
4- Copy password and click on download remote desktop file.
And login to Tokyo-Instance.
5- Search Firewall & network Protection.
6- Disable firewall & network protection.
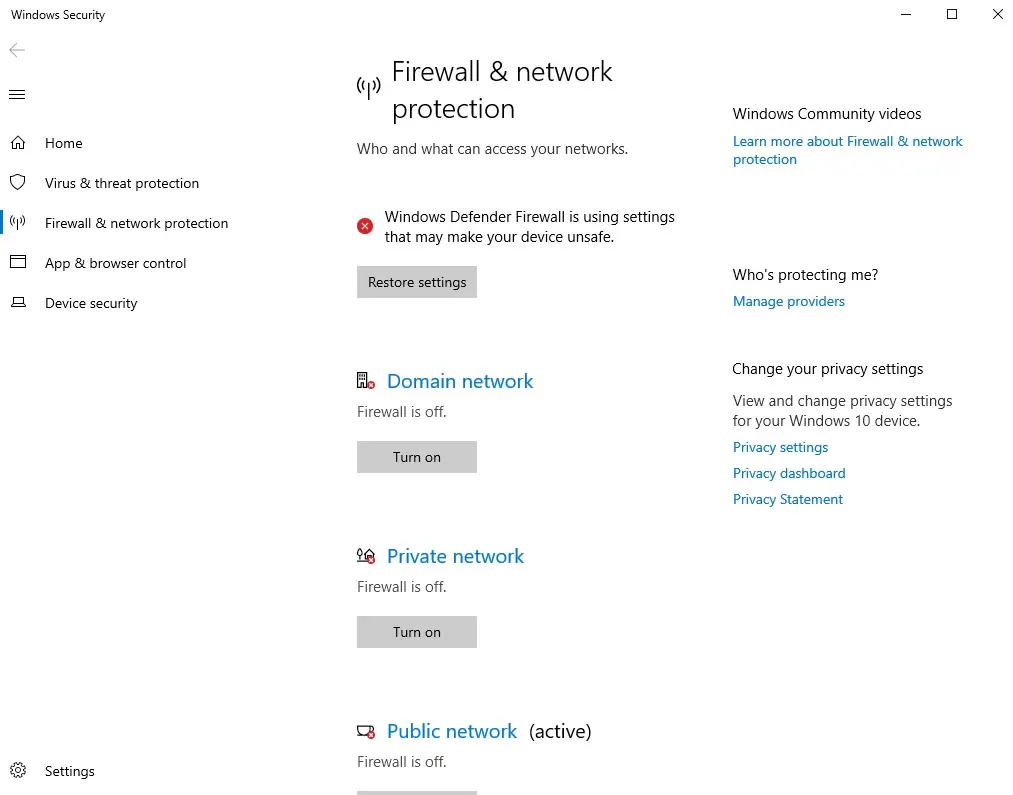
We have successfully tested the connectivity between these two regions using the ping command. We are able to ping the server each other without any issue.
Tokyo-Instance desktop.
Open command prompt and ping Ohio-Instance IP address.
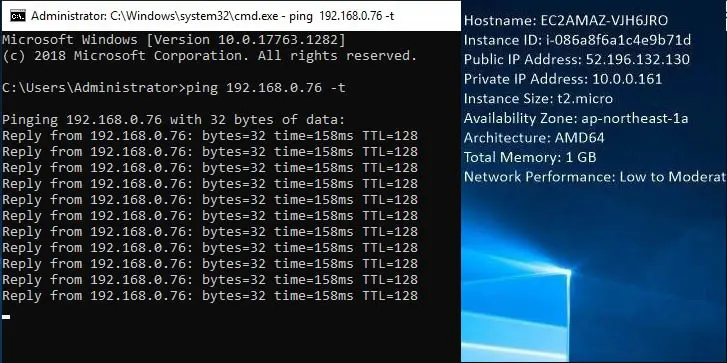
Ohio-Instance desktop.
Open command prompt and ping Tokyo-Instance IP address.
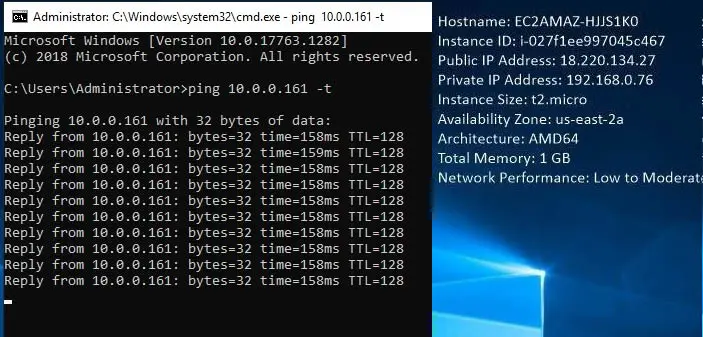
Related: How to Enable Cross Region Replication for Amazon S3.


