Adding an organization fails within the 401: Unauthorized and Connect to PowerShell Access Denied errors in Office 365 tenants with enabled Security Defaults
Require MFA (Multi-Factor Authentication) for all users, including administrators & Azure management. Require Azure MFA (Multi-Factor Authentication) registration
Block legacy authentication
Conditional Access: Require MFA for all users
Create a Conditional Access policy
The below steps will help you to create a Conditional Access policy to require All users to perform multi-factor authentication.
Adding an organization fails 401:
1- Signin Microsoft Azure as a security administrator, global administrator, or Conditional Access administrator. Select the Azure Active Directory
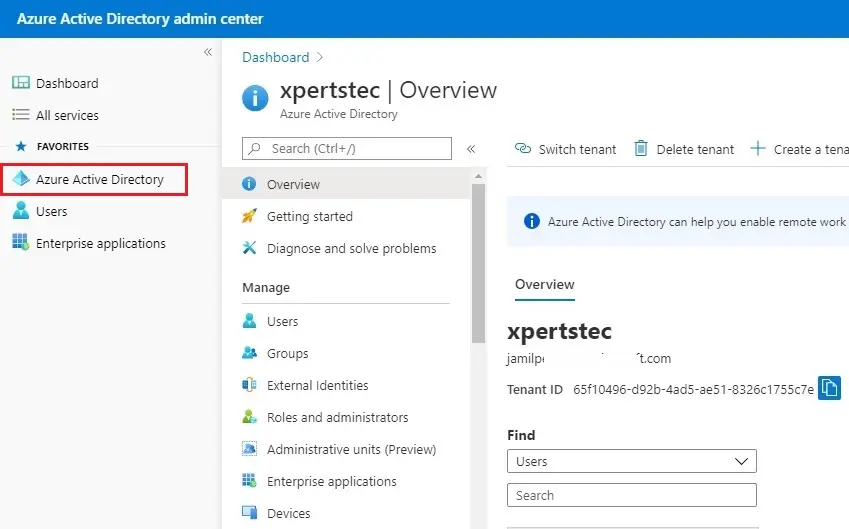
2- Select Security under manage tab.
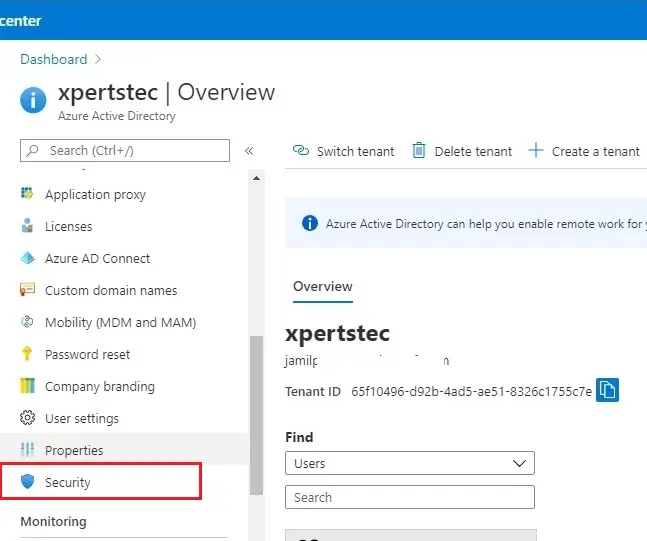
3- Under protect tab select Conditional Access.
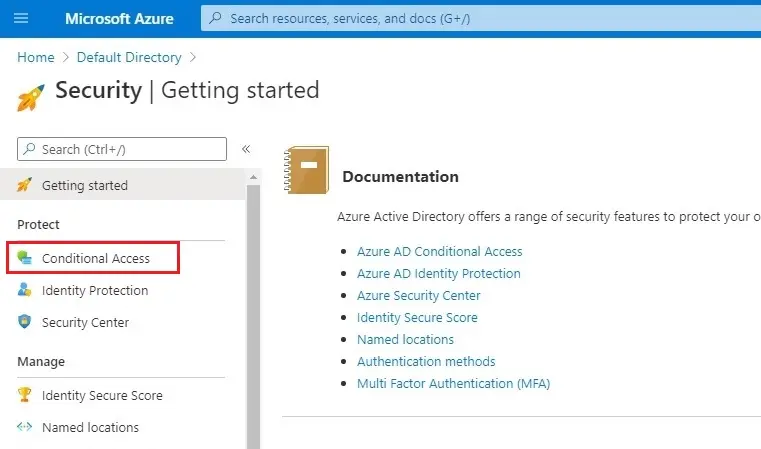
4- Click on + New policy.
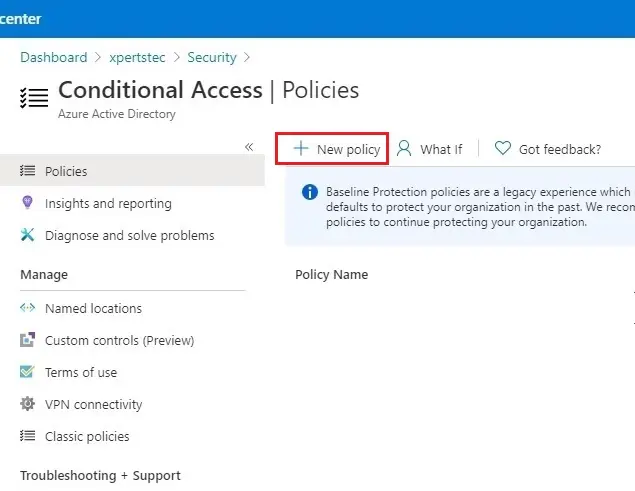
5- Type your policy a name. We recommend that institutional create a meaningful standard for the names of their policies.
Select Users and groups Under Assignments
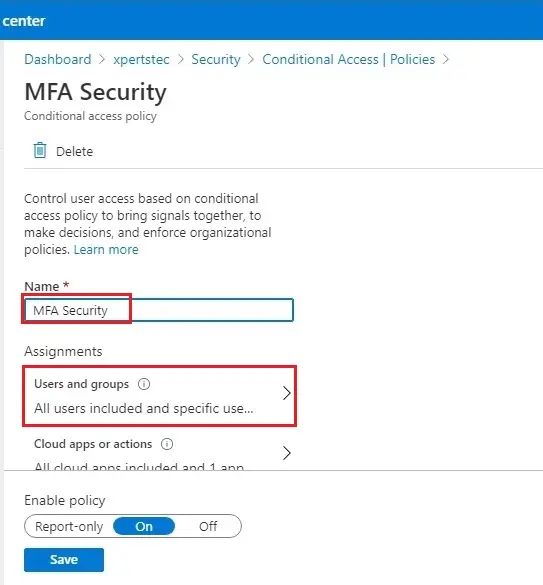
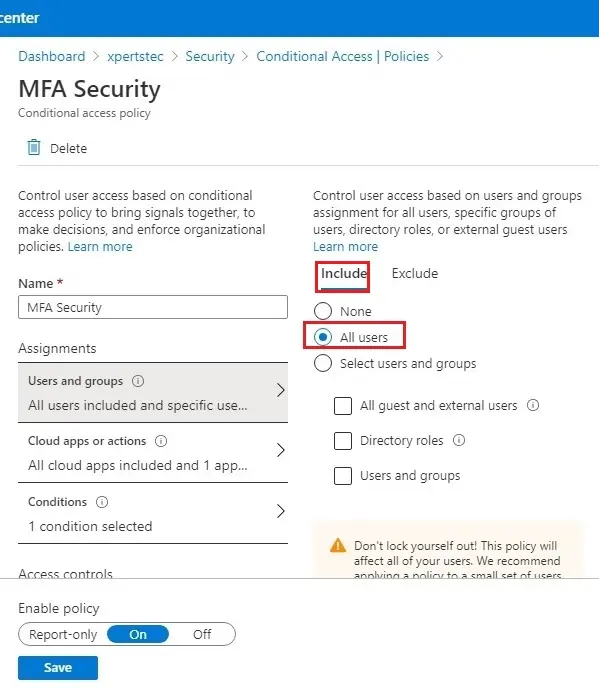
6- Select Include tab, and then select All users.
7- Select the Exclude tab and then select Users and Groups.
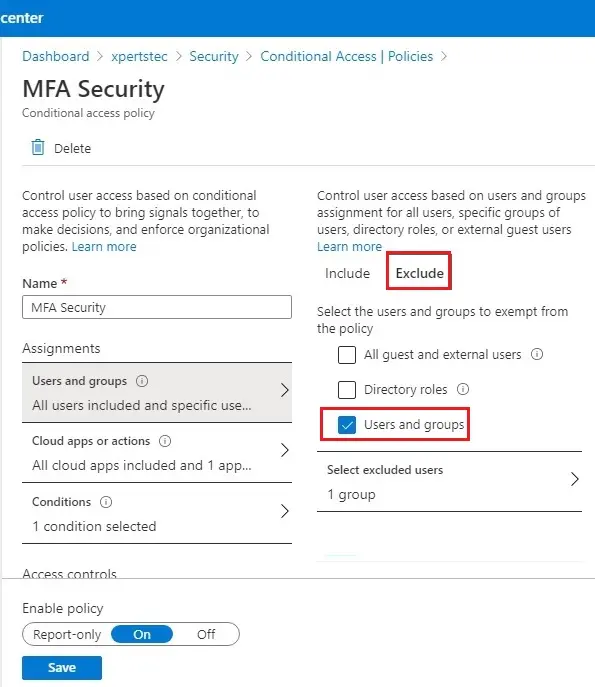
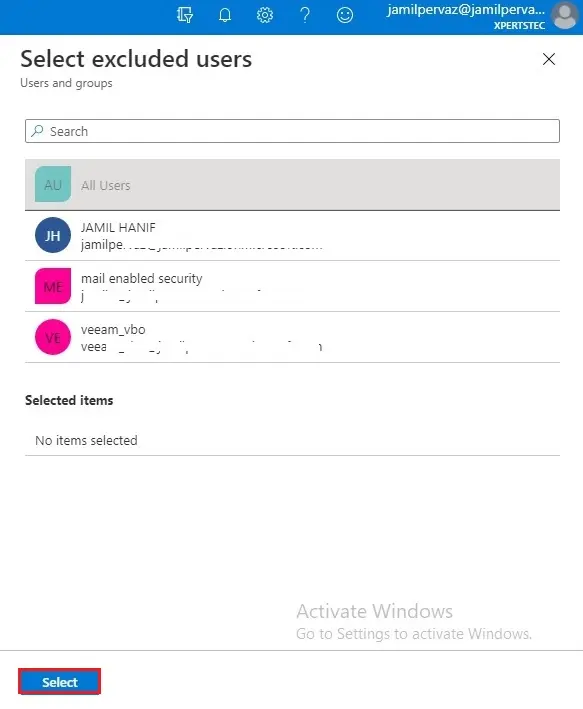
8- Select your organization’s emergency access or break-glass accounts and then choose the select button.
9- Select Cloud apps or actions, select Include and select All cloud apps.
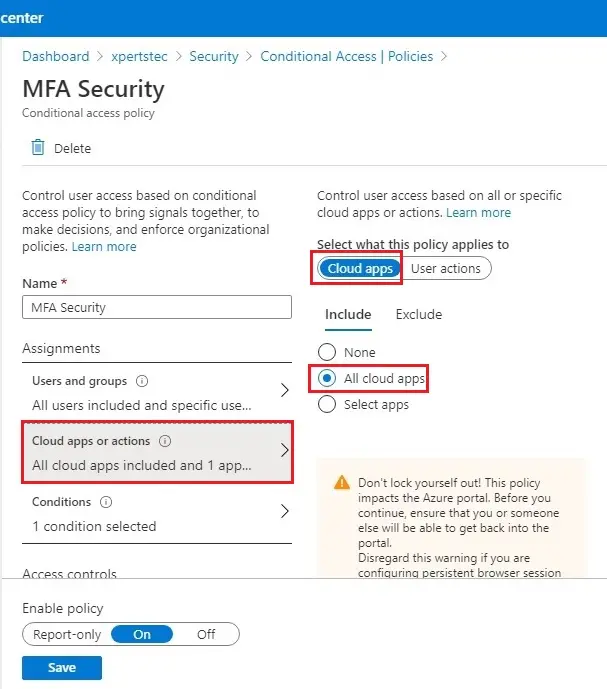
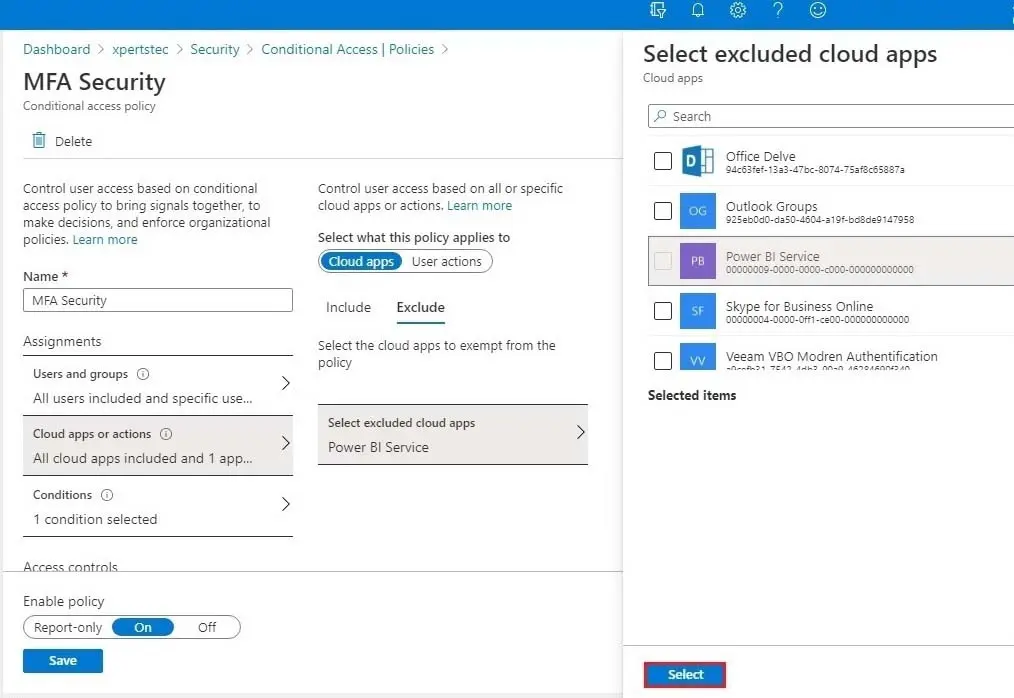
10- Select the Exclude tab, select excluded cloud apps, choose any applications that do not require multi-factor authentication, and click on the create button.
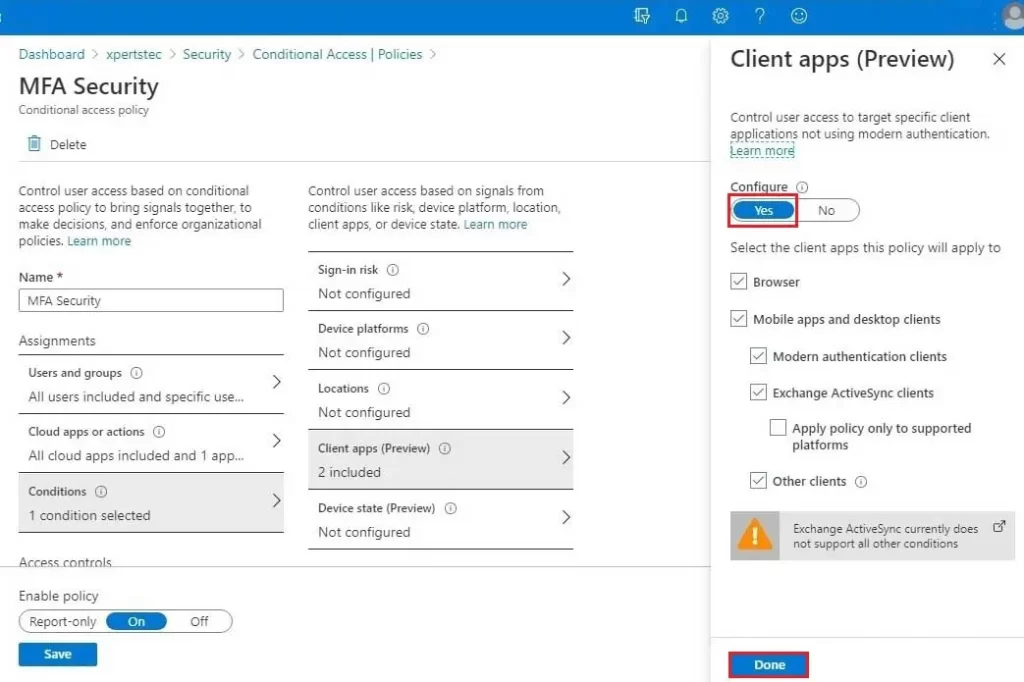
11- Choose the Conditions tab, select Client apps (Preview), and then select Configure to Yes. Under Select the client apps this policy will apply to leave all defaults selected and then select Done.
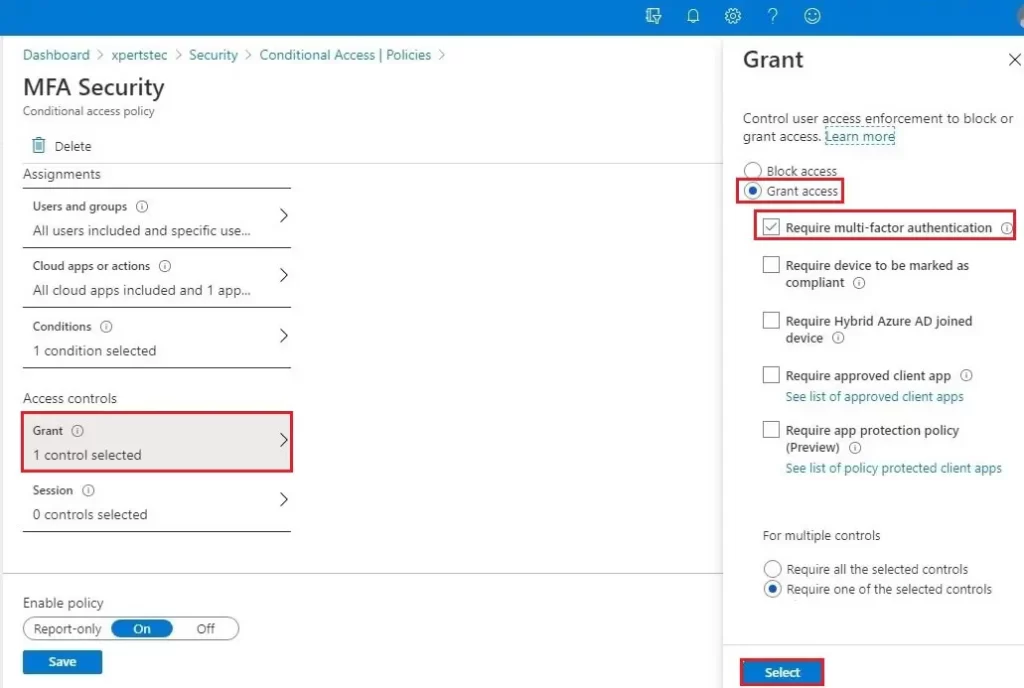
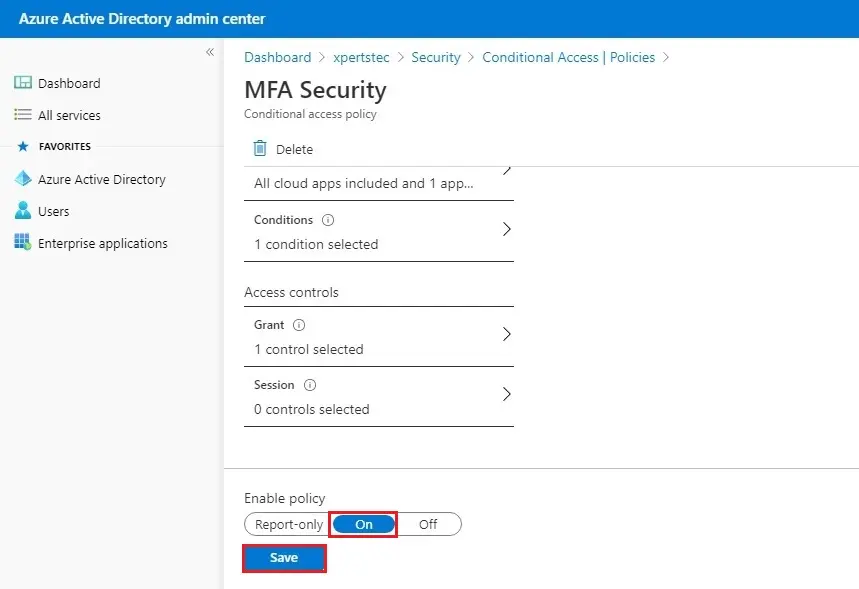
12- Under the Access controls option, select Grant, choose Grant access, select Require multi-factor authentication checkbox, and select Select.
13- Confirm your settings and choose Enable policy to On. Select Save to create to enable your policy.
For more details on adding an organization denied errors in Office 365 tenants, visit Veeam


