In this blog, I will show you how to configure network ACL in AWS. We are going to create a custom VPC network ACL for our VPC and explicitly DENY all access to our public subnet. ACL (Network access control) list is an optional layer of security for the VPC that acts as a firewall for controlling traffic in & out of one or further subnets. You might setup network ACLs with rules comparable to your security groups in order to add an additional layer of security to your VPC.
How to Create VPC Tokyo
1- Login to the AWS account and select AWS Services tab and then select VPC under Networking & Content Delivery.
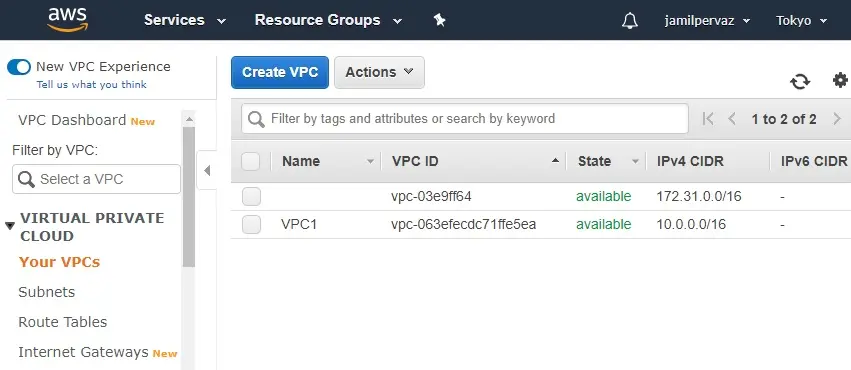
2- Under Virtual Private Cloud select Your VPCs
Click on Create VPC.
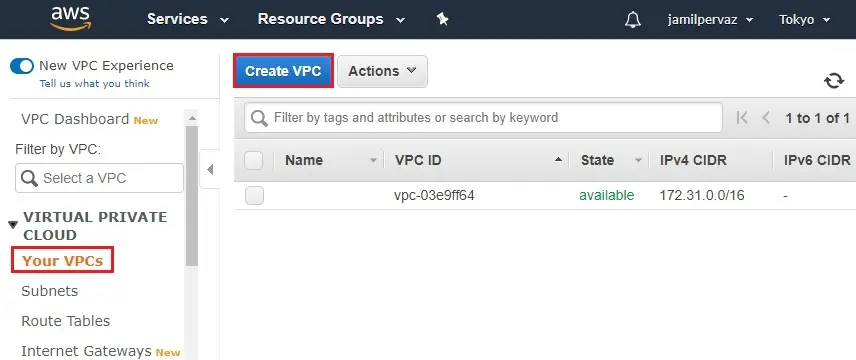
3- Create VPC wizard,
Name tag – VPC1
IPv4 CIDR block – 10.0.0.0/16.
Tenancy – default
Click Create
4- Click close.
5- Now you can see VPC successfully created.
How to Create Subnet
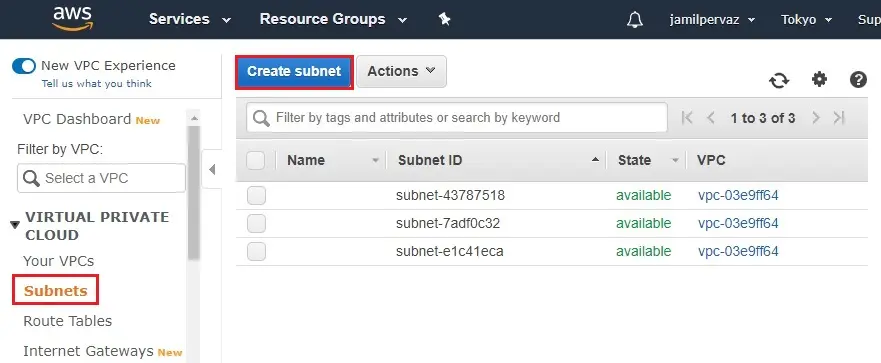
1- Select Subnets.
Choose Create Subnet.
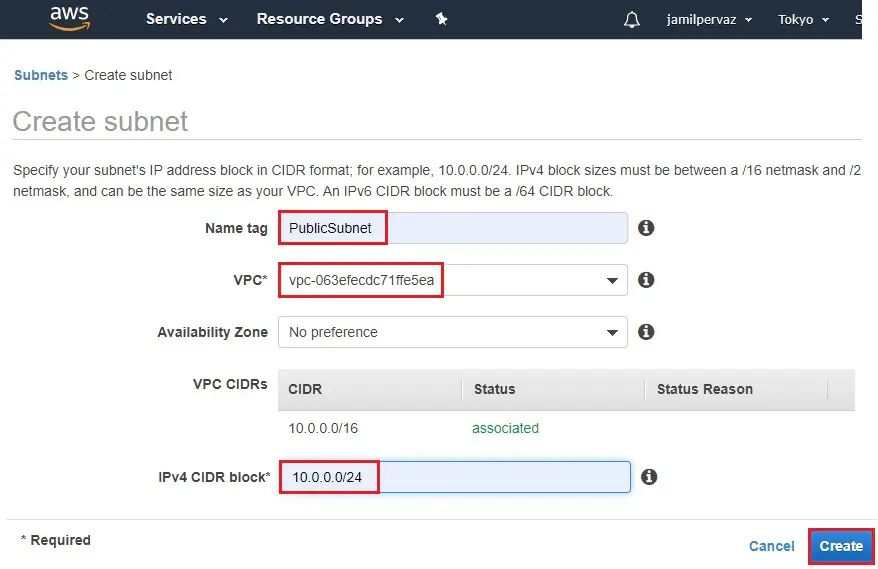
2- Name tag – PublicSubnet.
VPC – select the VPC1 that you created earlier.
Availability Zone
IPv4 CIDR block – enter a valid CIDR block. For example (10.0.0.0/24)
Click Create.
3- Click close
4- Subnets successfully created.
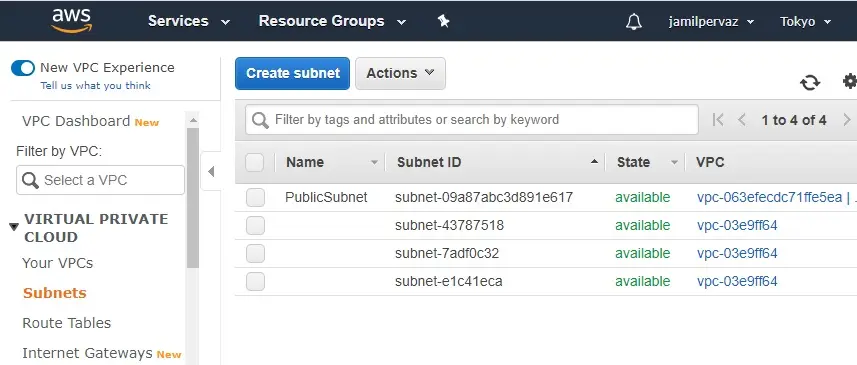
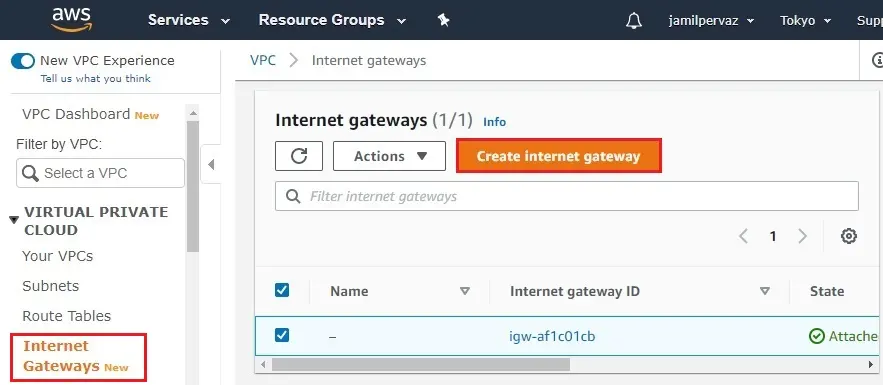
How to Create Internet Gateway
1- Click on Internet Gateways new on your left side and then click Create Internet Gateway.
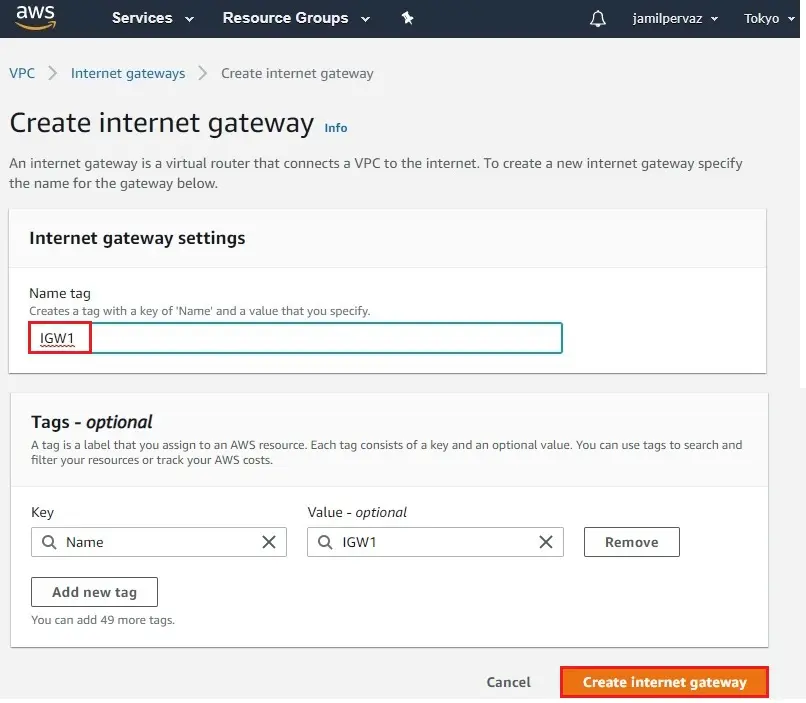
2- Enter a name (IGW1) in the Name tag text box and then click create internet gateway.
3- The internet gateway has been created and is in a detached state. We need to attach it to your VPC. In the action, menu select Attach to VPC.
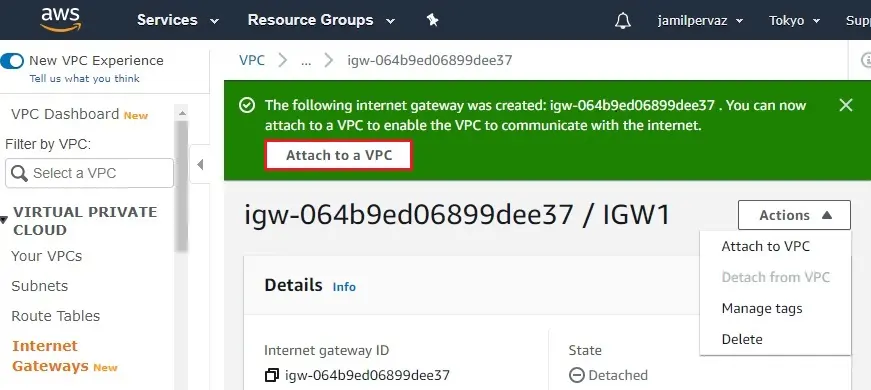
4- Choose your VPC1 from the drop-down menu and then click Attach internet gateway.
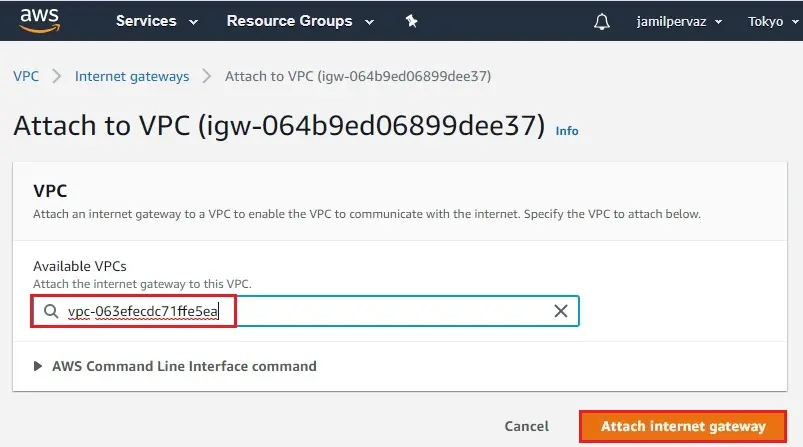
5- The internet gateway changes to the attached state.
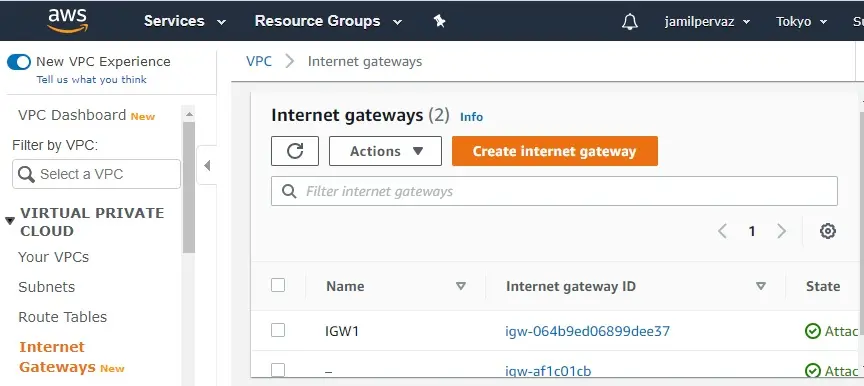
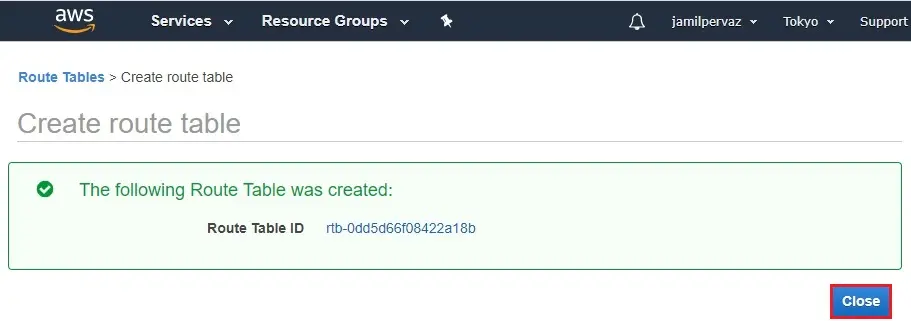
How to Create Route Table
1- Select Route Tables.
Click on Create route table.
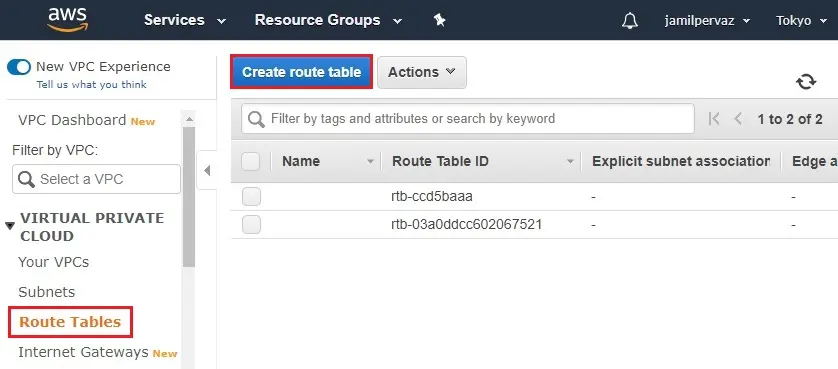
2- Name tag – enter a name for the route table (Public-Route).
VPC – Choose your VPC1, and then select Create.
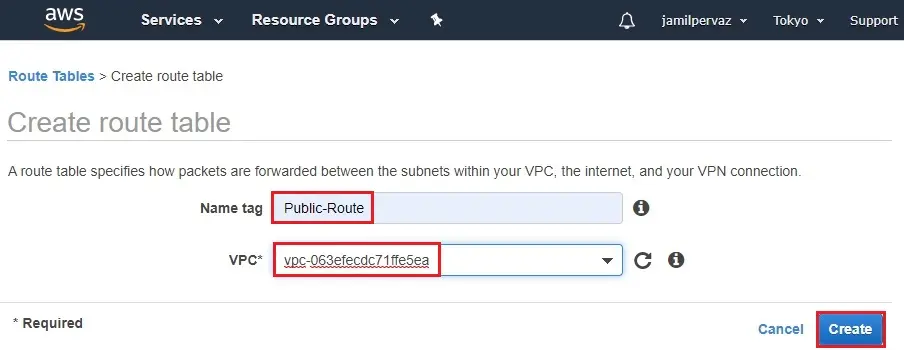
3- Click Close.
Configure Network ACL in AWS
Routing of public subnets
Now we need to configure the routing for the subnets. Enable traffic from your subnets to Internet by using the internet gateway attached to the VPC.
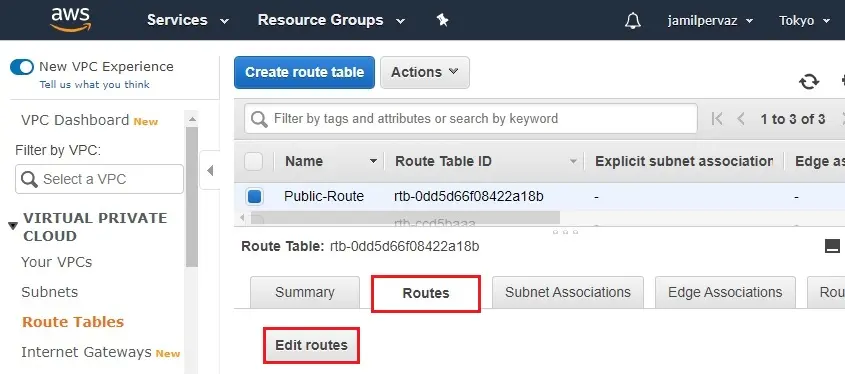
4- Choose Ohio-Route, Choose Routes tab and then click Edit routes.
Click Add route
The traffic from instances in the subnets predestined to the Internet will be redirected to the Internet Gateway.
Then we are redirected to the Route Table in the Virtual Private Cloud.
Add route for the Route Table – 1 for the traffic to the Internet to be routed using the Internet Gateway.
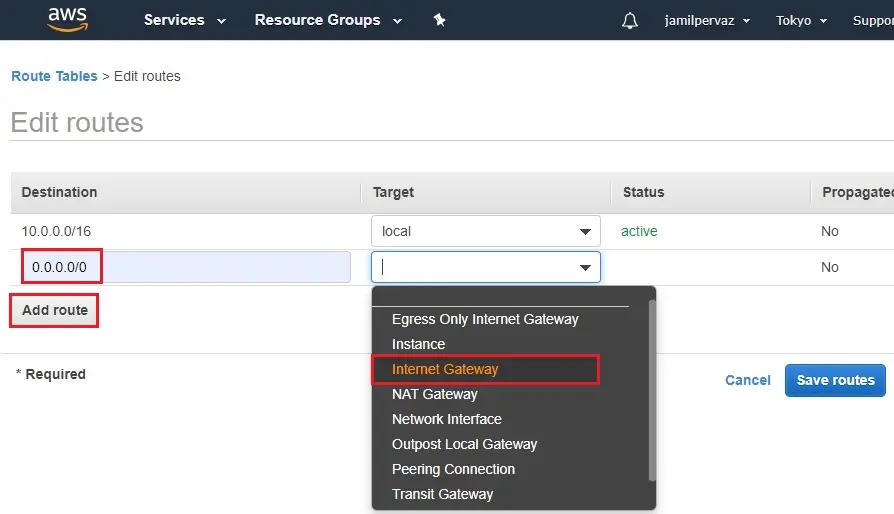
5- Select Add rules for destination type 0.0.0.0/0 (all packets for the internet) and then for targets select the Internet Gateway.
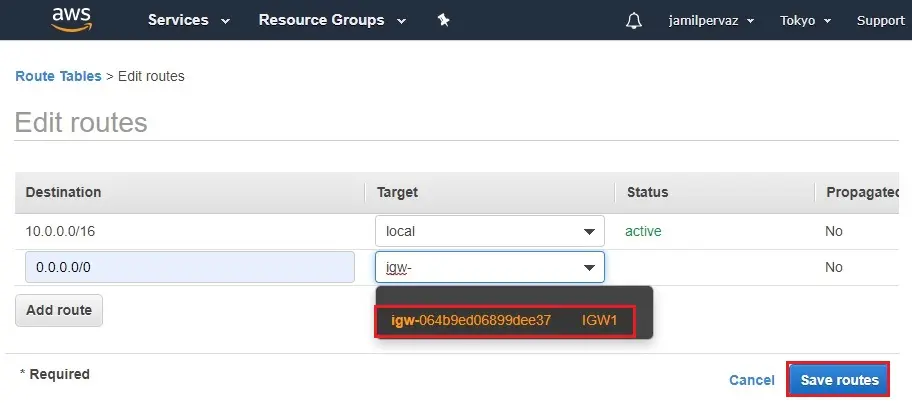
6- Select (IGW1) have created as in the earliest and then select save routes
7- Click close.
8- Successfully route edited
Choose Subnet Associations tab and then choose Edit Subnet associations.
9- Select your subnet (PublicSubnet) and then click Save.
10- Successfully edit subnet associations.
How to Create a Network ACL
Open the Amazon VPC console
1- Select Network ACLs under Security and then Create Network ACL.
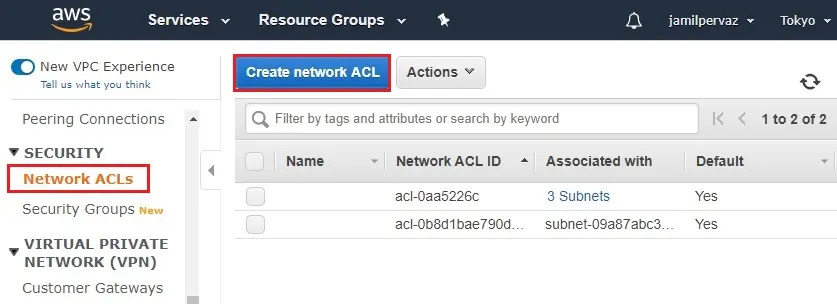
2- Create Network ACL wizard, type a name of your network ACL, and select the ID of your VPC (VPC1) from the list. Then select Yes, Create.
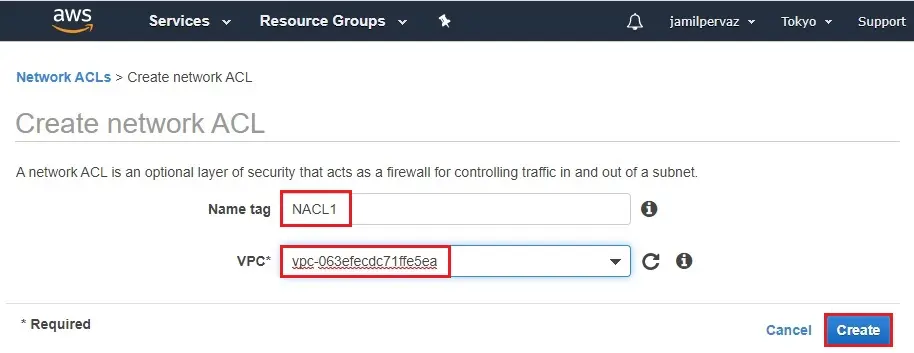
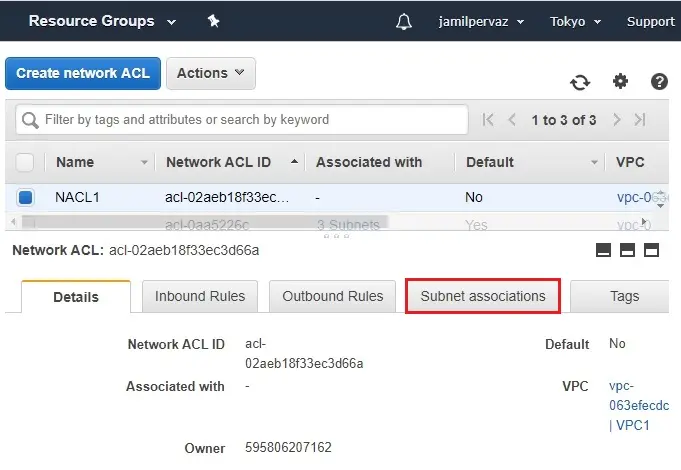
How to associate a subnet with a network ACL
3- Select subnet associations and then click edit subnet associations.
4- Select the subnet checkbox for the subnet to associate with the network ACL, and then choose Save.
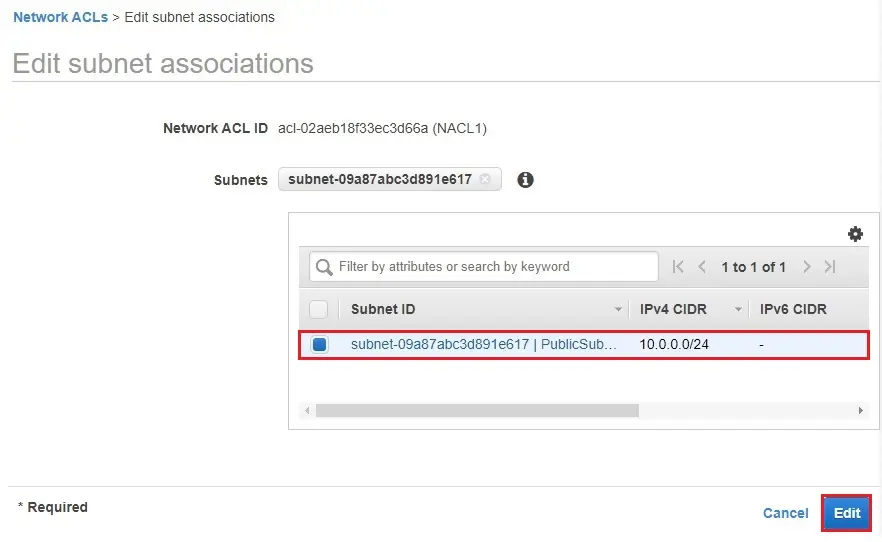
To add rules to a network ACL
5- Select Network ACLs, select Inbound Rules and then edit inbound rules.
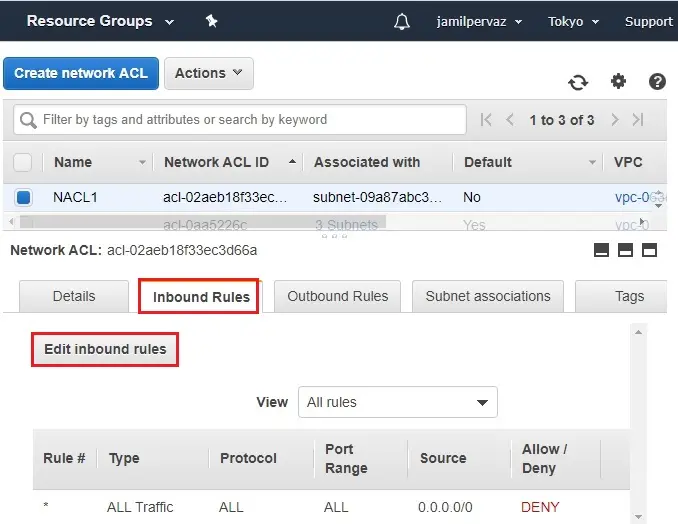
6- Click Add Rule.
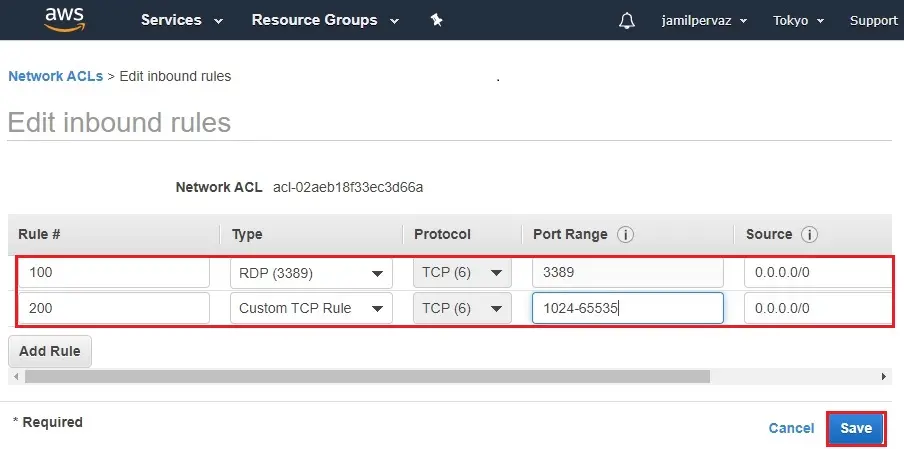
Enter a rule number (for example, 100). The rule number should not already be in use in the network ACL. We operation the rules in order, starting with the lowest number.
We recommend that we leave gaps between the rule numbers (example 100, 200, 300), rather than using sequential numbers (101, 102, 103). This take it easier adds a new rule without having to renumber the existing rules.
| Rule | Type | Protocol | Port Range | Destination |
| 100 | RDP (3389) | TCP (6) | 3389 | 0.0.0.0/0 |
| 200 | Custom TCP Rule | TCP (6) | 1024-65535 | 0.0.0.0/0 |
7- Select Save.
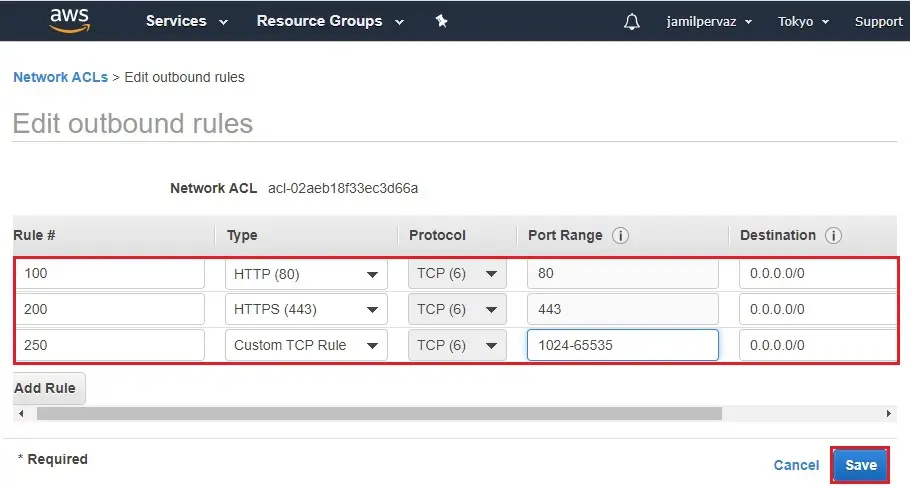
8- Select Outbound Rules tab, and then choose Edit outbound rules.
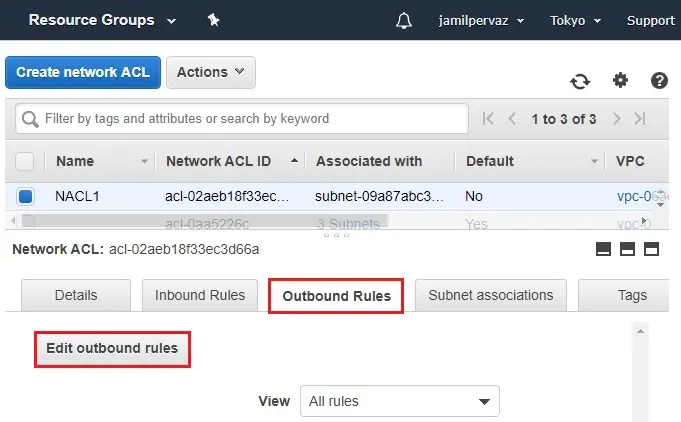
9- Click Add Rule.
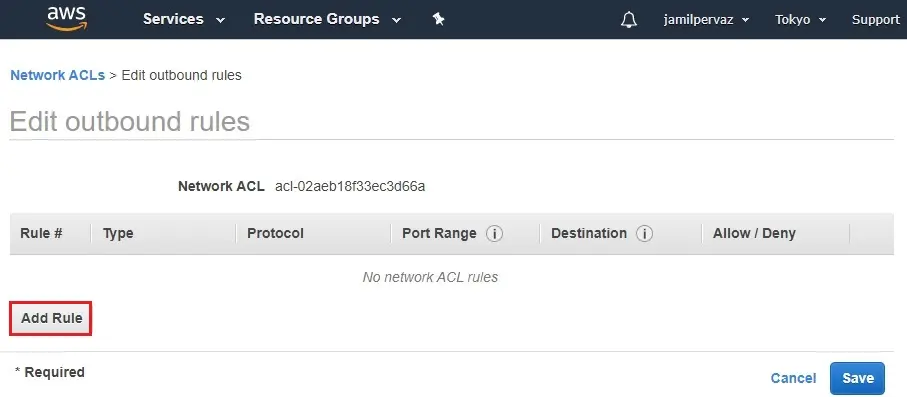
10- Edit Outbound Rule.
| Rule | Type | Protocol | Port Range | Destination |
| 100 | HTTP (80) | TCP (6) | 80 | 0.0.0.0/0 |
| 200 | HTTPS (443) | TCP (6) | 443 | 0.0.0.0/0 |
| 250 | Custom TCP Rule | TCP (6) | 1024-65535 | 0.0.0.0/0 |
11- Select Save.
Create Instance
1- Select service tab, click on EC2 under compute.
2- Click on Launch Instance button.
3- Select Microsoft Windows Server 2019.
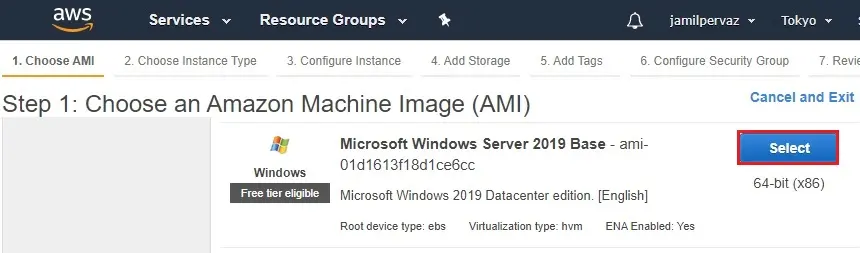
3- Choose t2 micro.
Click Next : Configure Instance details
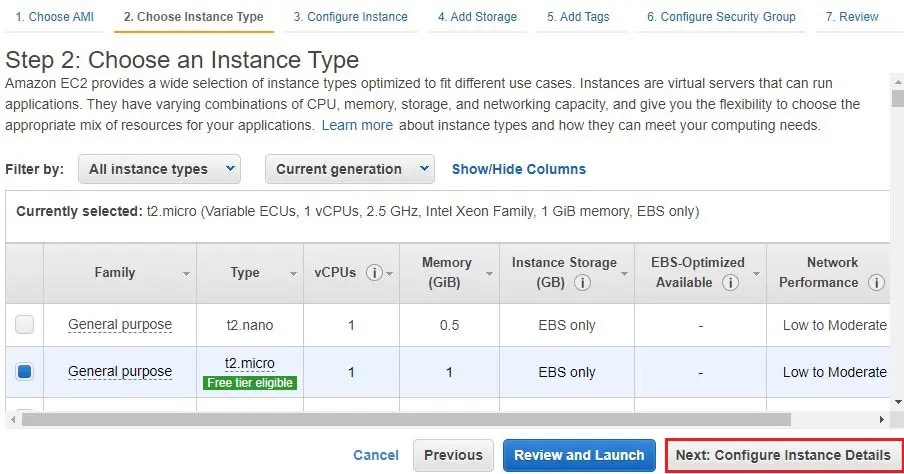
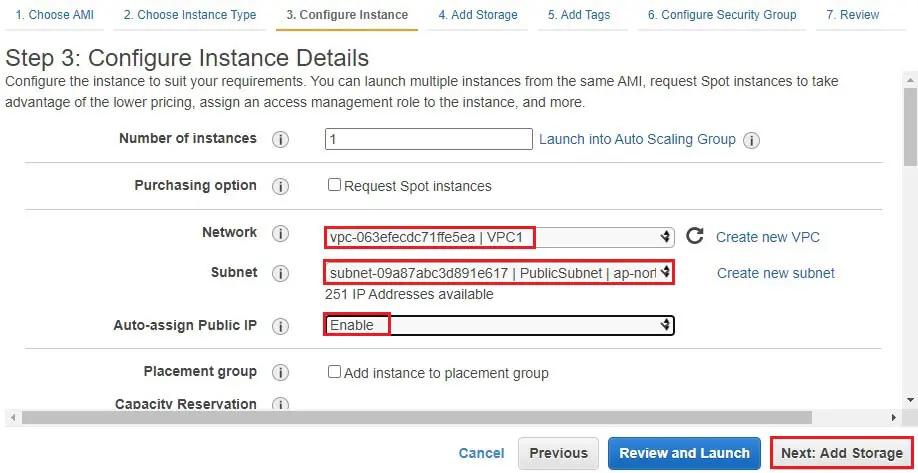
5- Network – select VPC (VPC1).
Subnets – select PublicSubnet.
Auto Assign Public IP – select Enable.
Click on Next : Add Storage.
6- Click Next : Add Tags.
7- Click on Next : Configure Security Groups.
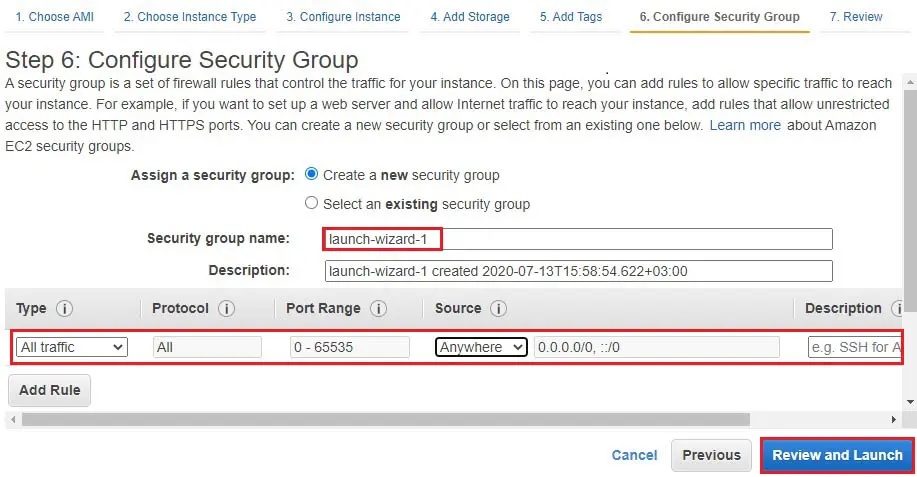
8- I keep it default Security
Select Protocols ALL traffic, Protocol all, Port Range (0-65535) Select Source Anywhere
Click on Review and Launch.
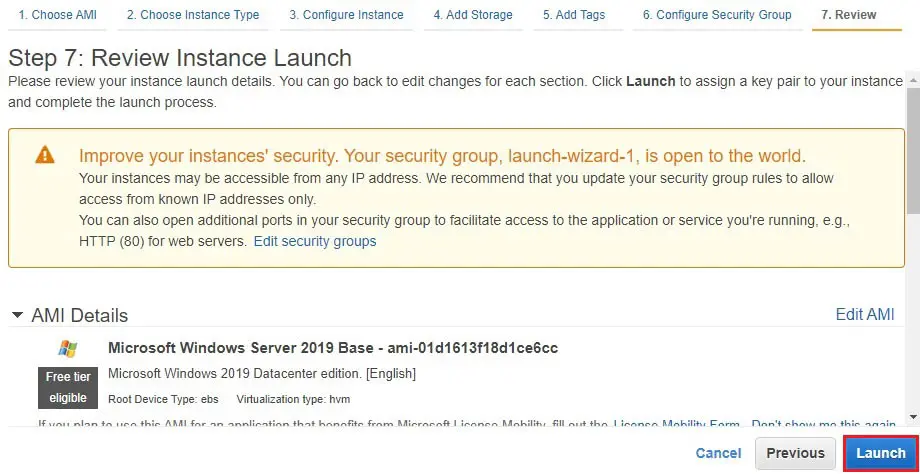
9- Review the instance details, parameters and then click launch.
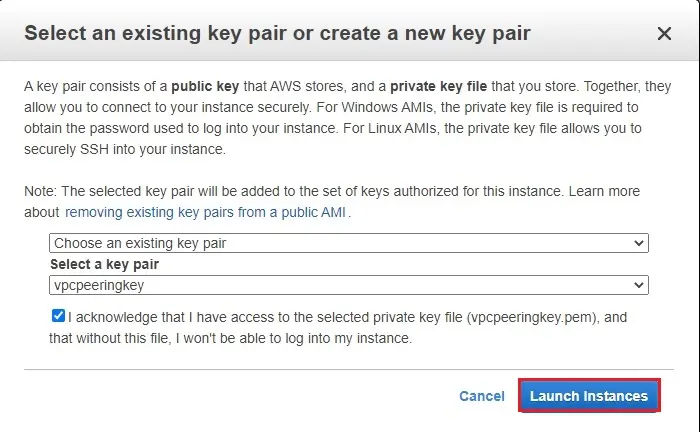
10- I am using existing key pair
Click launch instance.
Related: How to create Instance in AWS
Testing Configure Network ACL in AWS
1- Select Instance and then click connect.
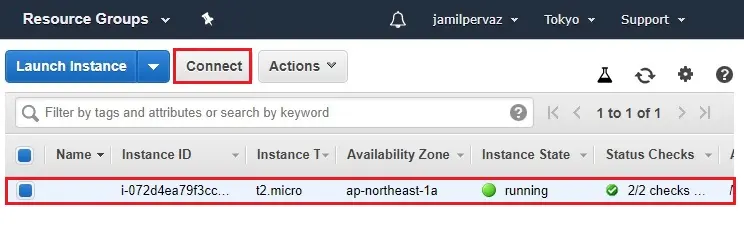
1- Select Get Password
Select choose file, choose your key pair, and then click decrypt password
Copy password and then choose download remote desktop file.
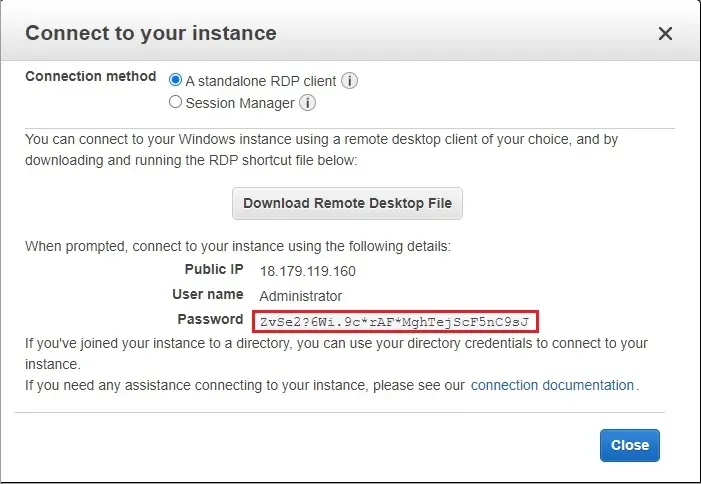
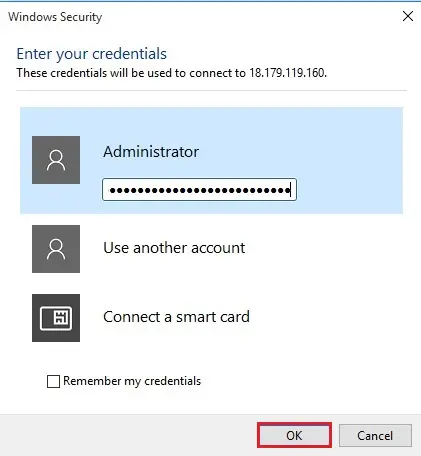
3- And login to Instance.
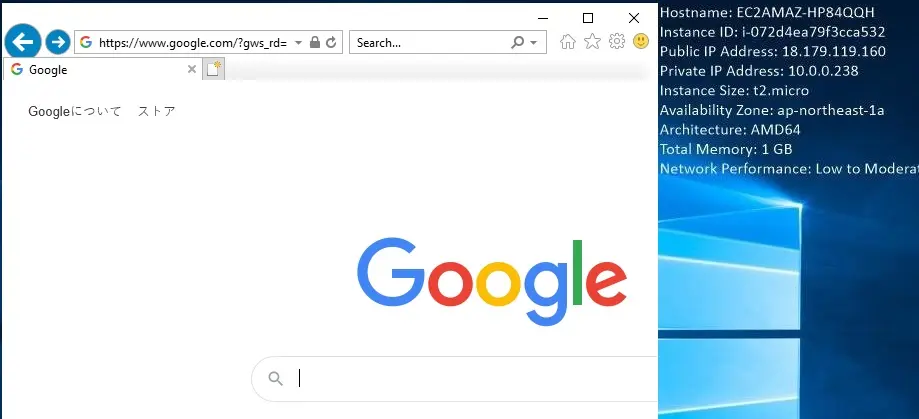
4- Now you can see internet is working.
Related: What is AMI in AWS and How to Create AMI from an EC2 Instance.


